免费试用 30 天
功能比较
| Standard | Premium | |
| Protect against data loss proactively | ||
| Feature | Standard | Premium |
| Enforced single sign-on (SSO) ? | Standard ✓ | Premium ✓ |
| SCIM automated user provisioning ? | Standard ✓ | Premium ✓ |
| Authentication policies ? | Standard ✓ | Premium ✓ |
| External user security ? | Standard ✓ | Premium ✓ |
| Enforced two-step verification ? | Standard ✓ | Premium ✓ |
| Mobile app management (MAM) ? | Standard ✓ | Premium ✓ |
| API token controls ? | Standard ✓ | Premium ✓ |
| Data security policies ? | Standard ✓ | Premium ✓ |
| Data classification ? | Standard - | Premium ✓ |
| Enforce data security policies by classification ? | Standard - | Premium ✓ |
| Detect and investigate suspicious activity | ||
| Feature | Standard | Premium |
| Automatic product discovery ? | Standard ✓ | Premium ✓ |
| Organization insights ? | Standard ✓ | Premium ✓ |
| Organization audit log: Admin activity ? | Standard ✓ | Premium ✓ |
| Comprehensive organization audit log: User activity, API tokens, Webhooks ? | Standard - | Premium ✓ |
| Anomalous activity detections ? | Standard - | Premium ✓ |
| Content scanning ? | Standard - | Premium ✓ |
| SIEM integrations ? | Standard - | Premium ✓ |
| Alert messaging integrations ? | Standard - | Premium ✓ |
| Respond to threats before they become incidents | ||
| Feature | Standard | Premium |
| Alert investigations ? | Standard - | Premium ✓ |
| Actor profiles ? | Standard - | Premium ✓ |
| Remediation recommendations ? | Standard - | Premium ✓ |
| Remediation workflows ? | Standard - | Premium ✓ |
| Alert hand-off ? | Standard - | Premium ✓ |
See Atlassian Guard in action
Atlassian Access 功能
| 针对所有受管理用户强制执行单一登录 (SSO),以允许这些用户通过公司现有身份提供程序向 Atlassian Cloud 产品进行身份验证。这意味着,用户可以使用同一组凭据访问多个工具,同时使用一种更安全的身份验证方法而不只是用户名和密码。 |
| 通过 SCIM 调配和取消调配实现用户生命周期管理自动化。对 Atlassian Cloud 产品的访问权限将由您在外部目录中设置的规则来定义。 当员工加入公司或调至新团队时,用户调配可以减少向他们授予应用程序访问权限时需要的手动操作。 |
| 管理员可以设置身份验证策略来管理会话时长、单一登录 (SSO)、密码策略和双重验证。可以创建多个策略并将其应用于受管理账户的不同子集。 |
| 强制性的双重验证可以作为身份验证策略的一部分应用。这要求组织中的用户必须开启双重验证,才能登录和访问他们的 Atlassian Cloud 产品。 |
| 使用移动应用管理 (MAM) 创建和管理可应用于受管理和非受管理用户的安全策略。可以在组织级别设置策略,也可以为特定用户指定策略,以提供额外的安全控制,例如禁用屏幕截图、数据导出限制和设备加密要求。 |
| 通过探索组织中的受管理用户何时在 Atlassian Cloud 产品中创建实例,了解影子 IT。自动产品发现功能可识别产品管理员以及有多少用户在使用这些产品。 |
| 组织审核日志是对 Atlassian Cloud 组织中所有管理员活动的全面记录。组织审核日志向管理员显示管理活动的人员、内容和时间,以帮助组织跟踪和识别任何可疑行为。 |
| 将 Atlassian Access 与您的 CASB 集成,以便获得在 Atlassian 中的登录和管理活动的完整记录。抵御常见威胁,例如用户凭据泄露、密码不够健全或与权限过高的帐户有关的内部威胁。 了解有关如何连接 McAfee MVISION 或 Microsoft Defender CASB 的更多信息。 |
Enforced single sign-on (SSO)
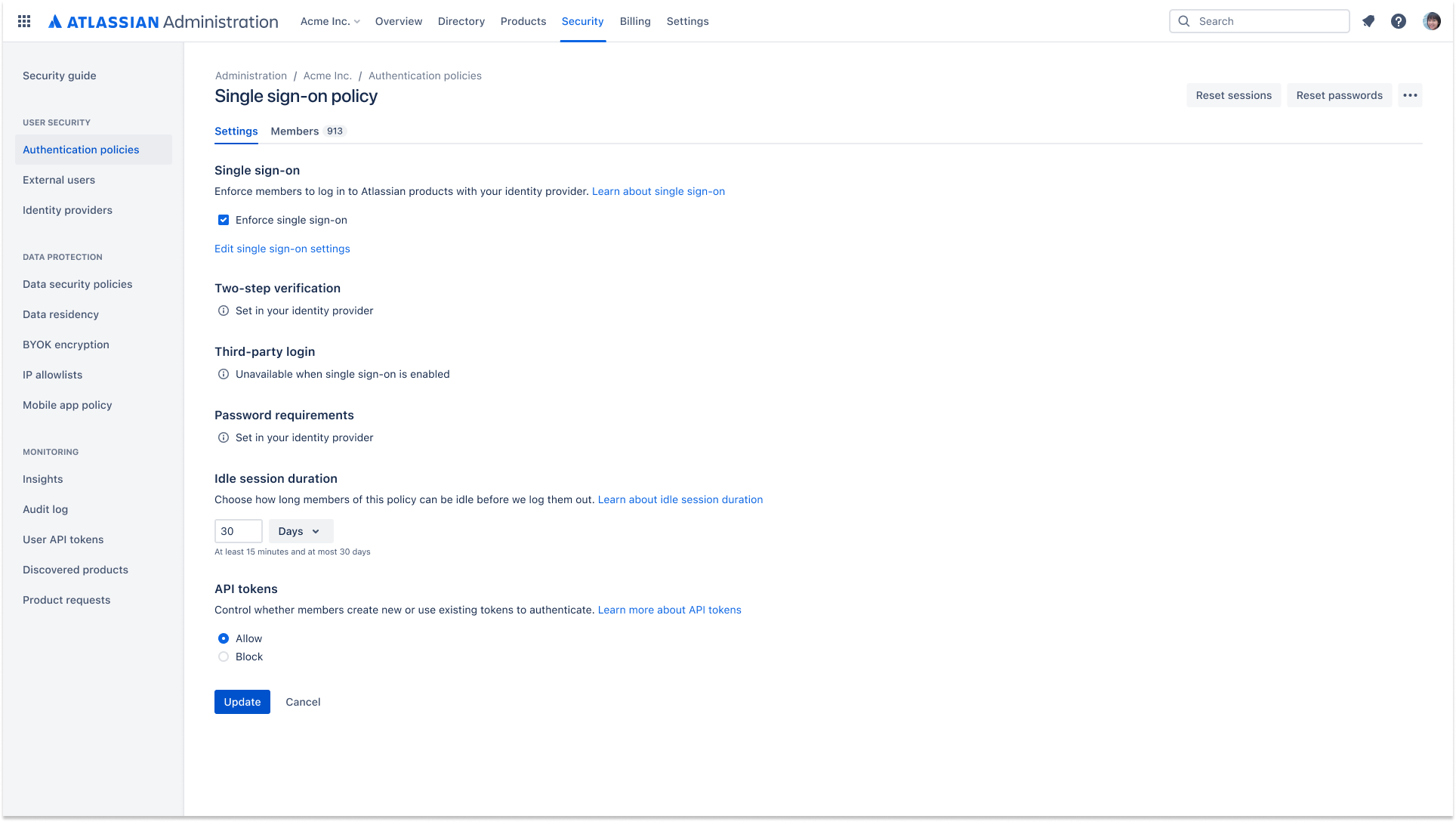
注意:为简便起见,此表格仅显示最多 5,000 个用户。Access 没有用户限额。请使用定价计算器计算超过 5,000 个用户时的年度定价。
SCIM automated user provisioning
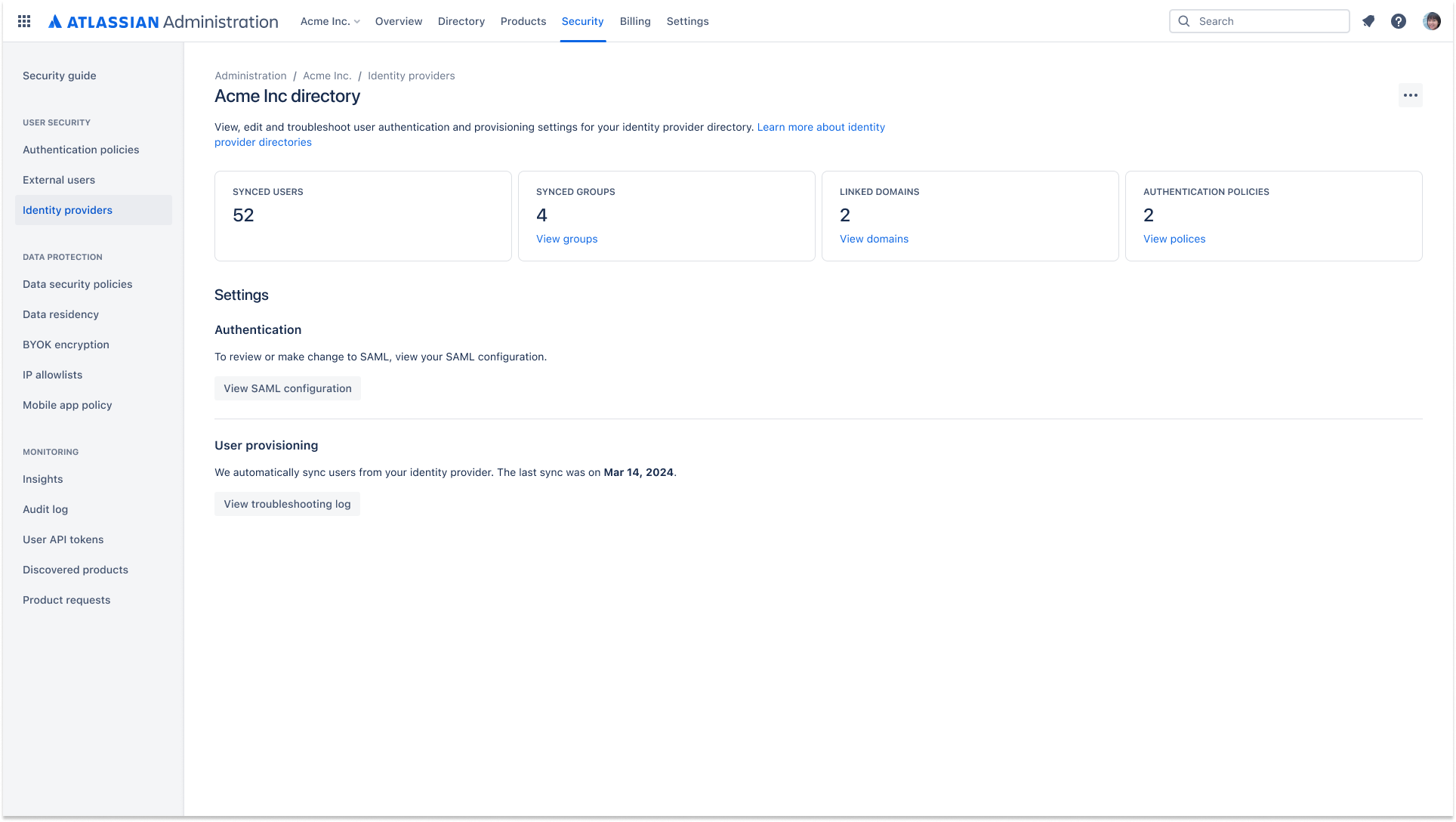
Automate user lifecycle management with SCIM provisioning and de-provisioning. Access to Atlassian cloud products will be defined by rules set in your external directory.
Authentication policies
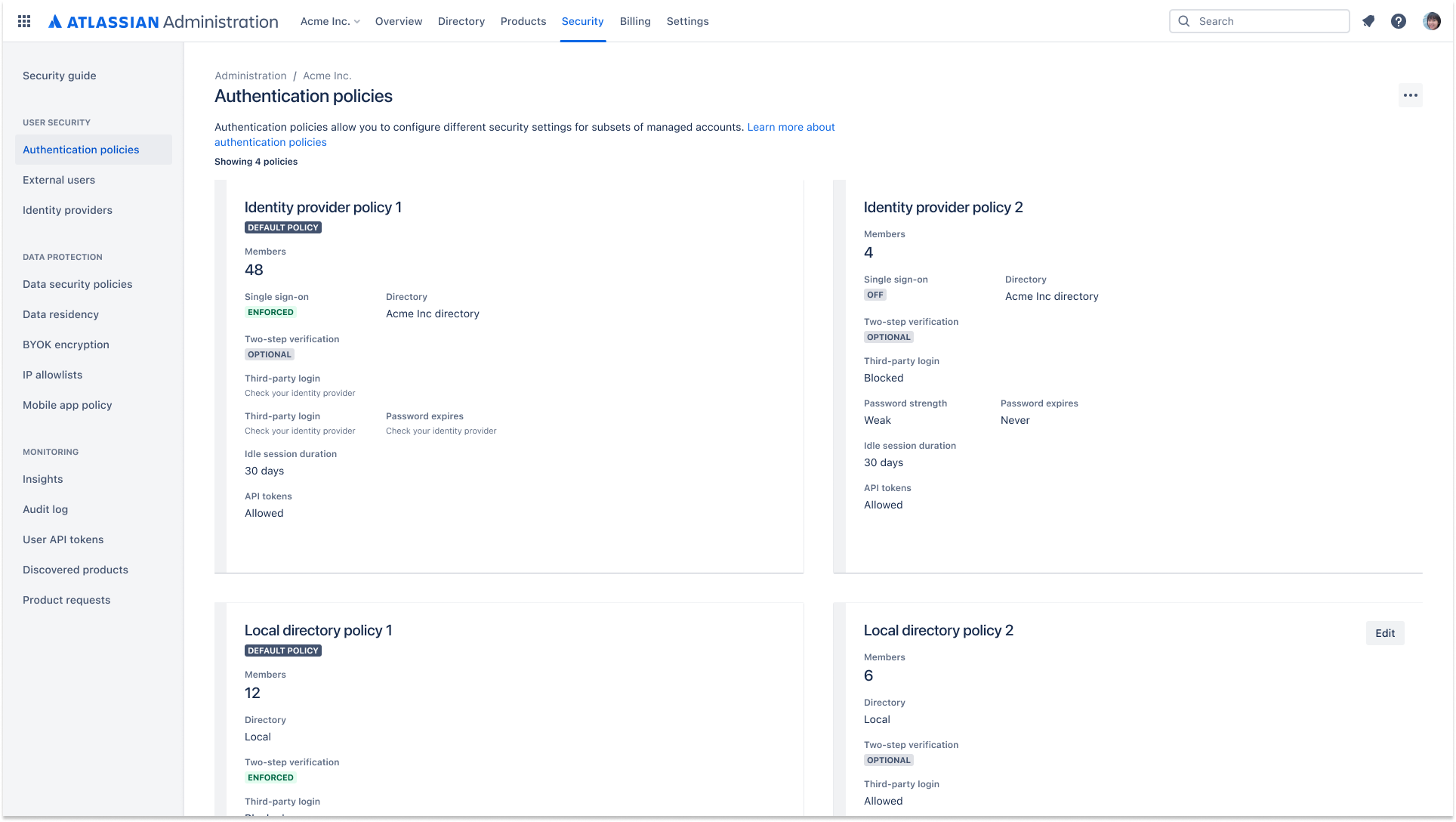
Admins can set authentication policies to manage session duration, single sign-on (SSO), password policies, and two-step verification. Multiple policies can be created and applied to different subsets of managed accounts.
External user security
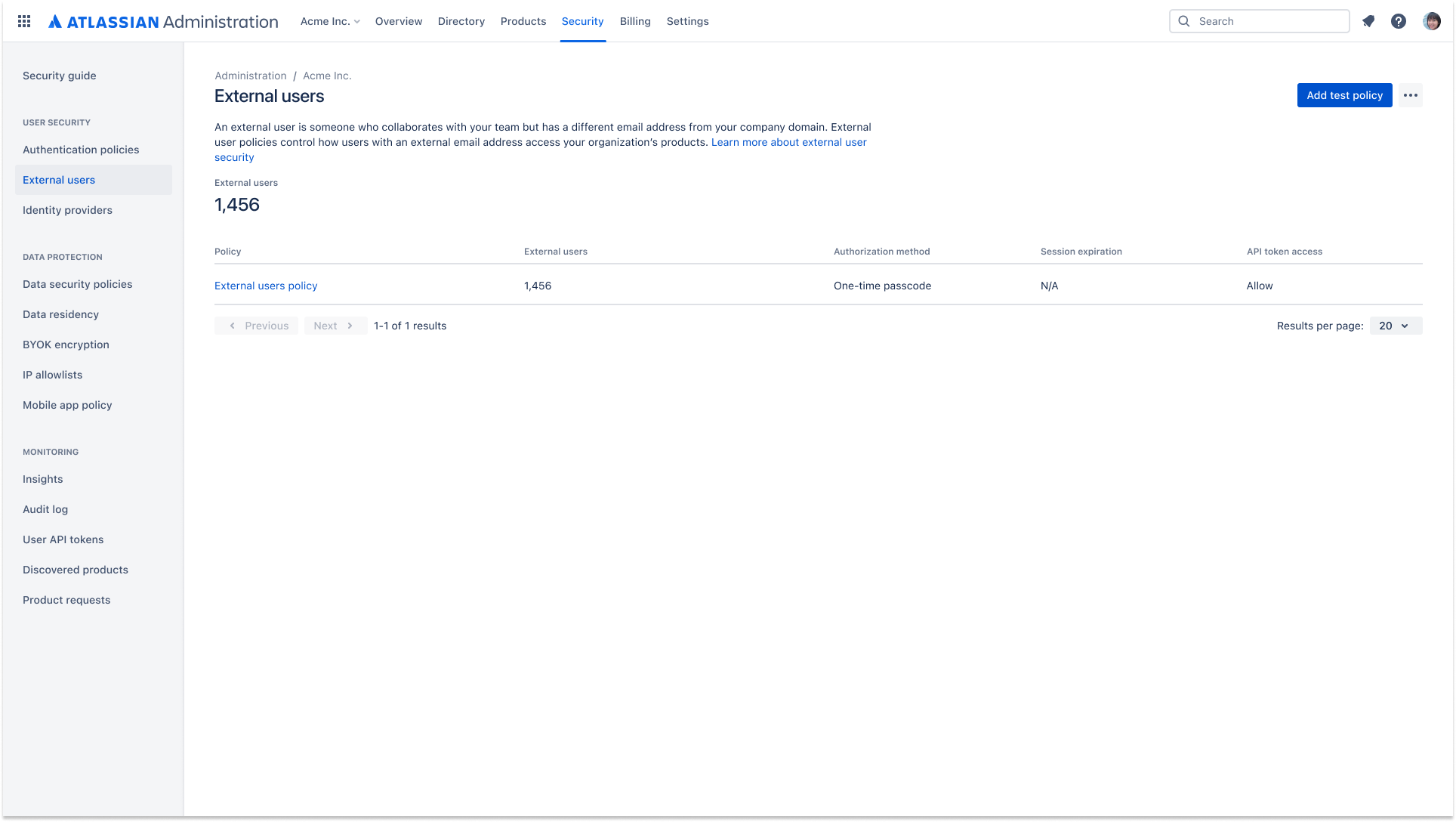
An external user policy allows you to apply security settings, including two-step verification, to external users. The settings apply to all the external users in your Atlassian organization.
Mobile app management (MAM)
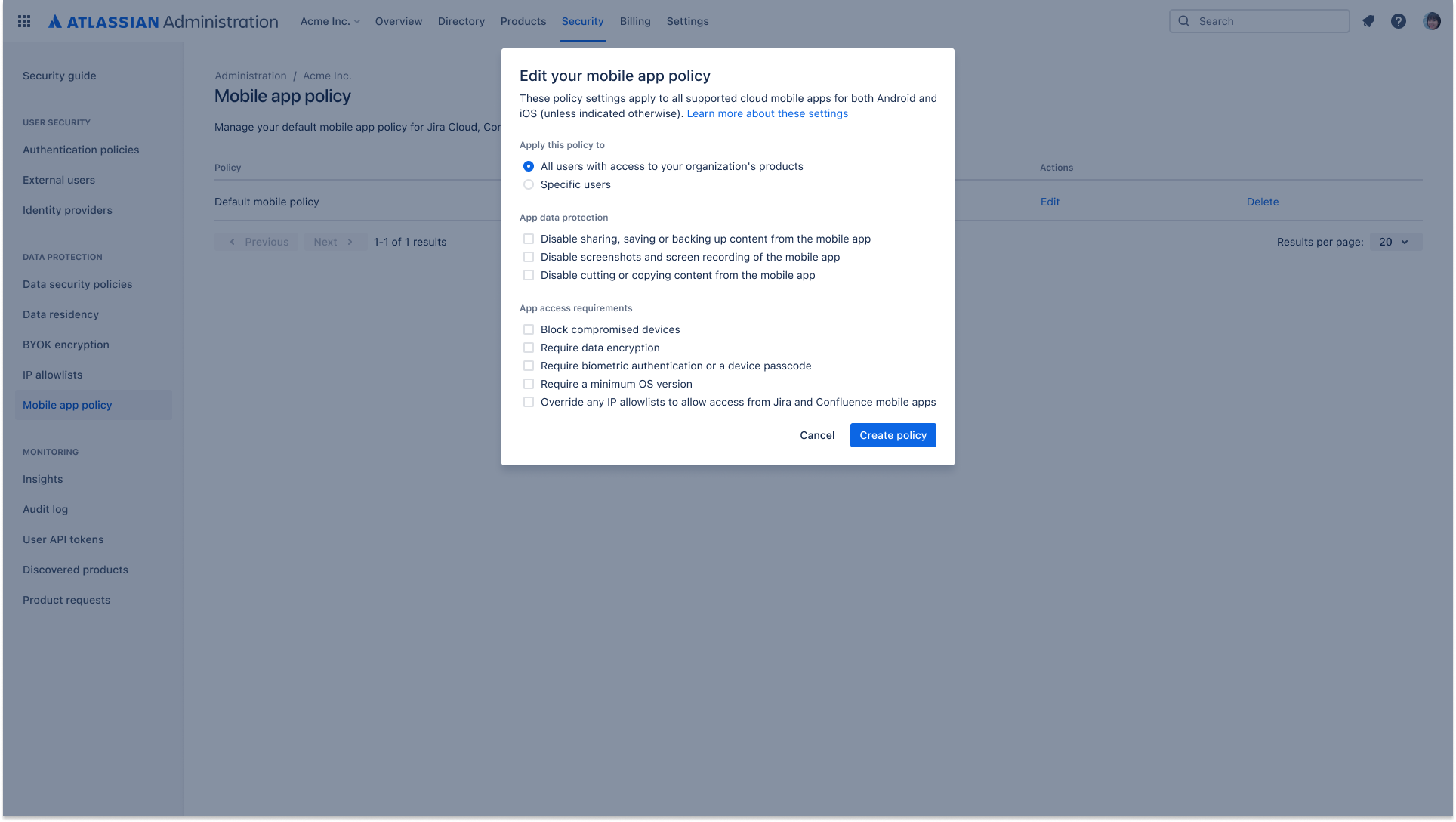
Create and manage security policies that can be applied to both managed and unmanaged users with mobile app management (MAM). Policies can be set at the organization level, or designated for select users to provide additional security controls such as screenshot disabling, data export restrictions and device encryption requirements
API token controls
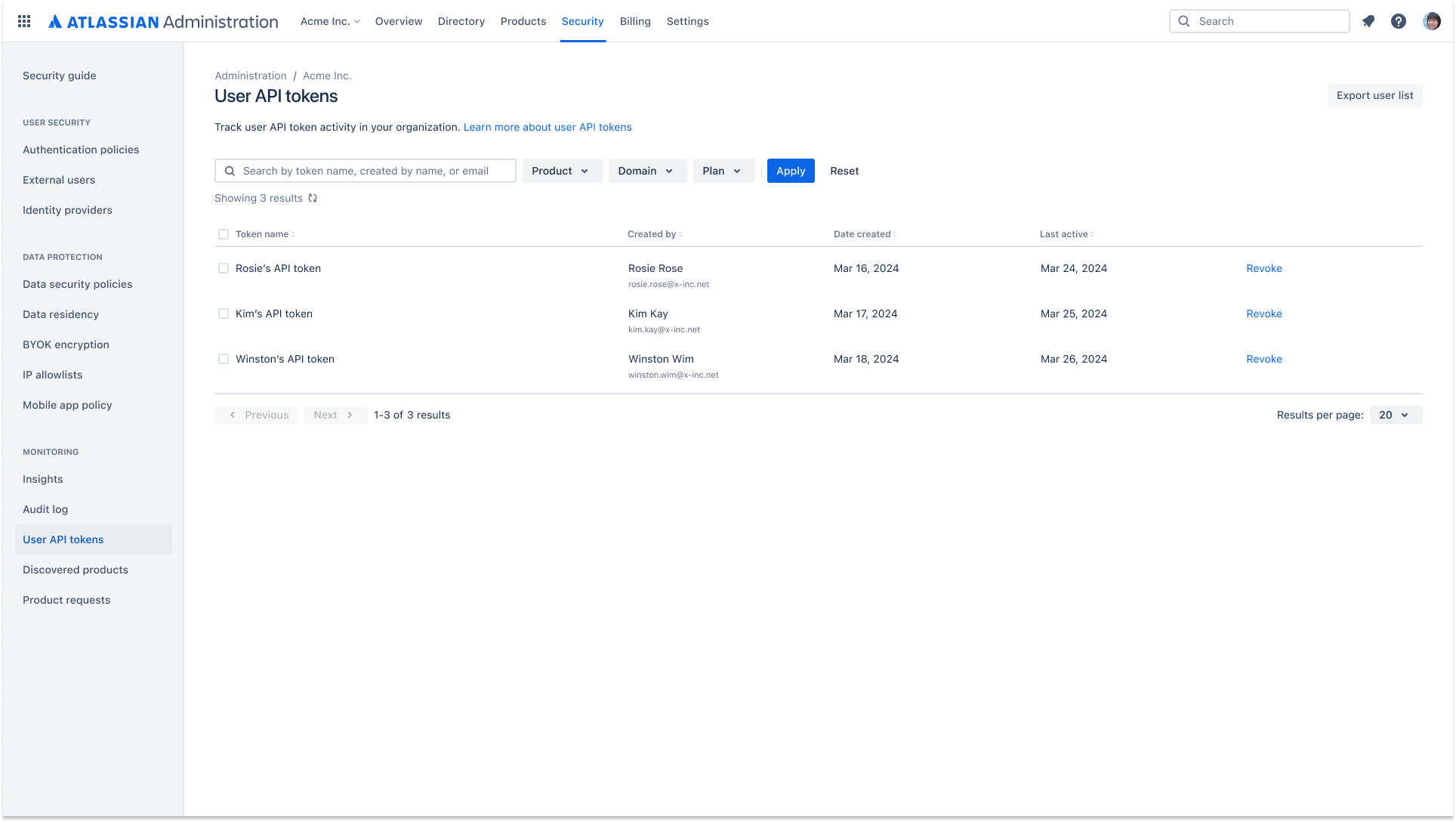
Admins have greater visibility and control over API token management and its lifecycle. This includes controlling which users can create an API token to access data and viewing which users are creating and revoking API tokens.
Data security policies
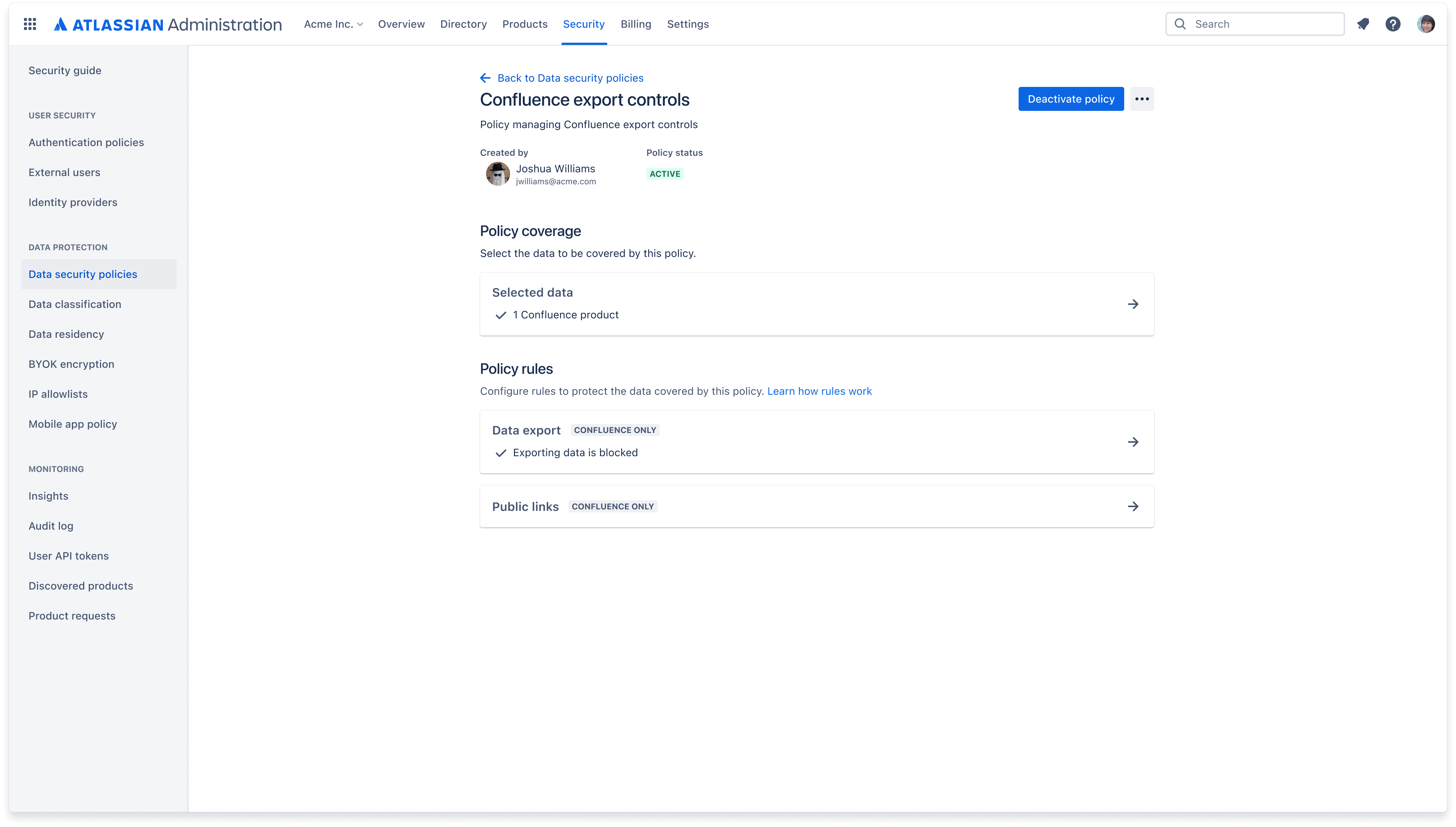
A data security policy helps you keep your organization’s data secure. Create policies to govern how users, apps, and people outside of your organization can interact with content such as Confluence pages and Jira issues.
Data classification
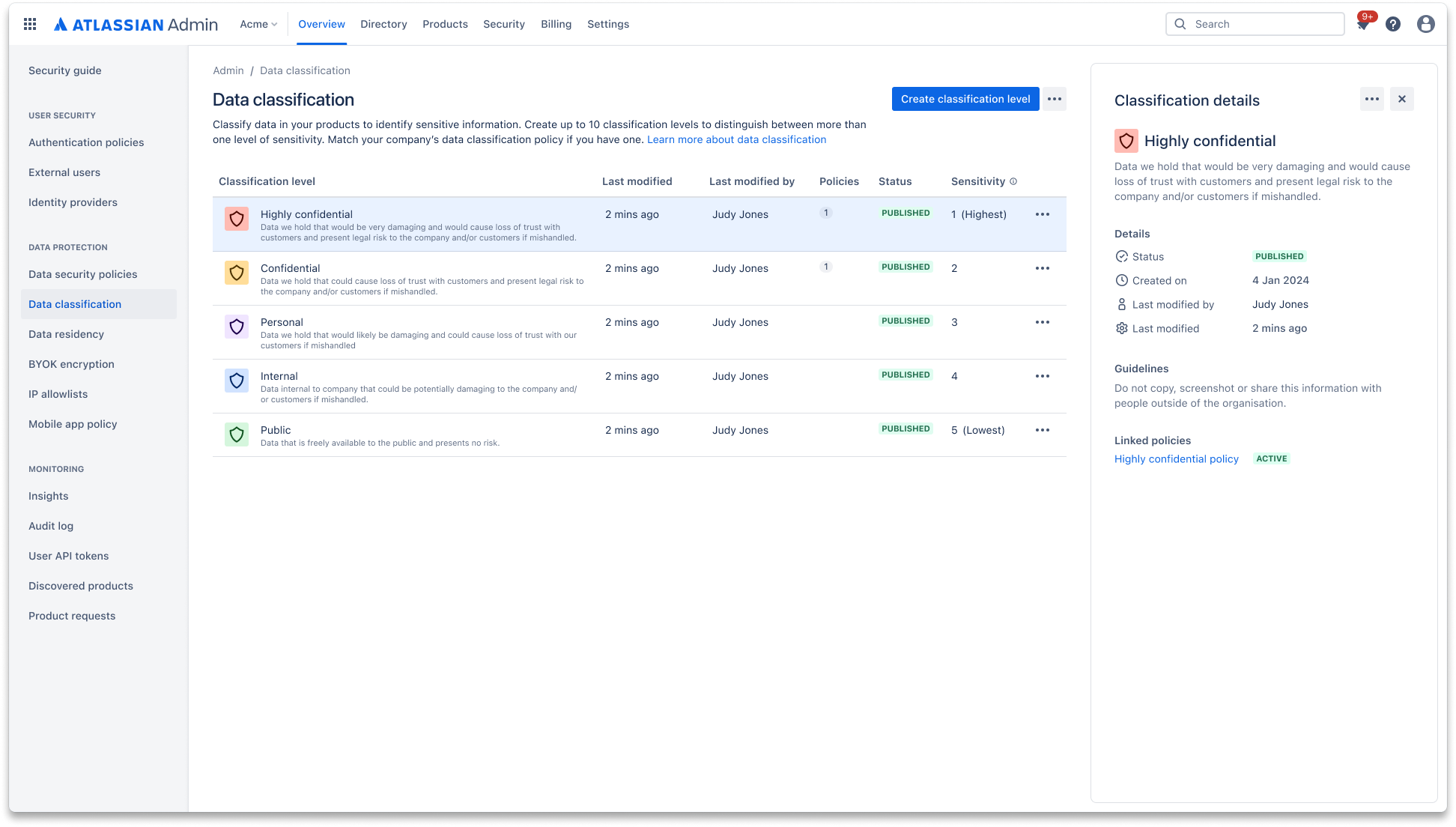
Data classification allows admins to define their data governance approach and label critical data accordingly within Atlassian products. Admins can set data security policies and rules to control user interaction based on data classification level.
Enforce data security policies by classification
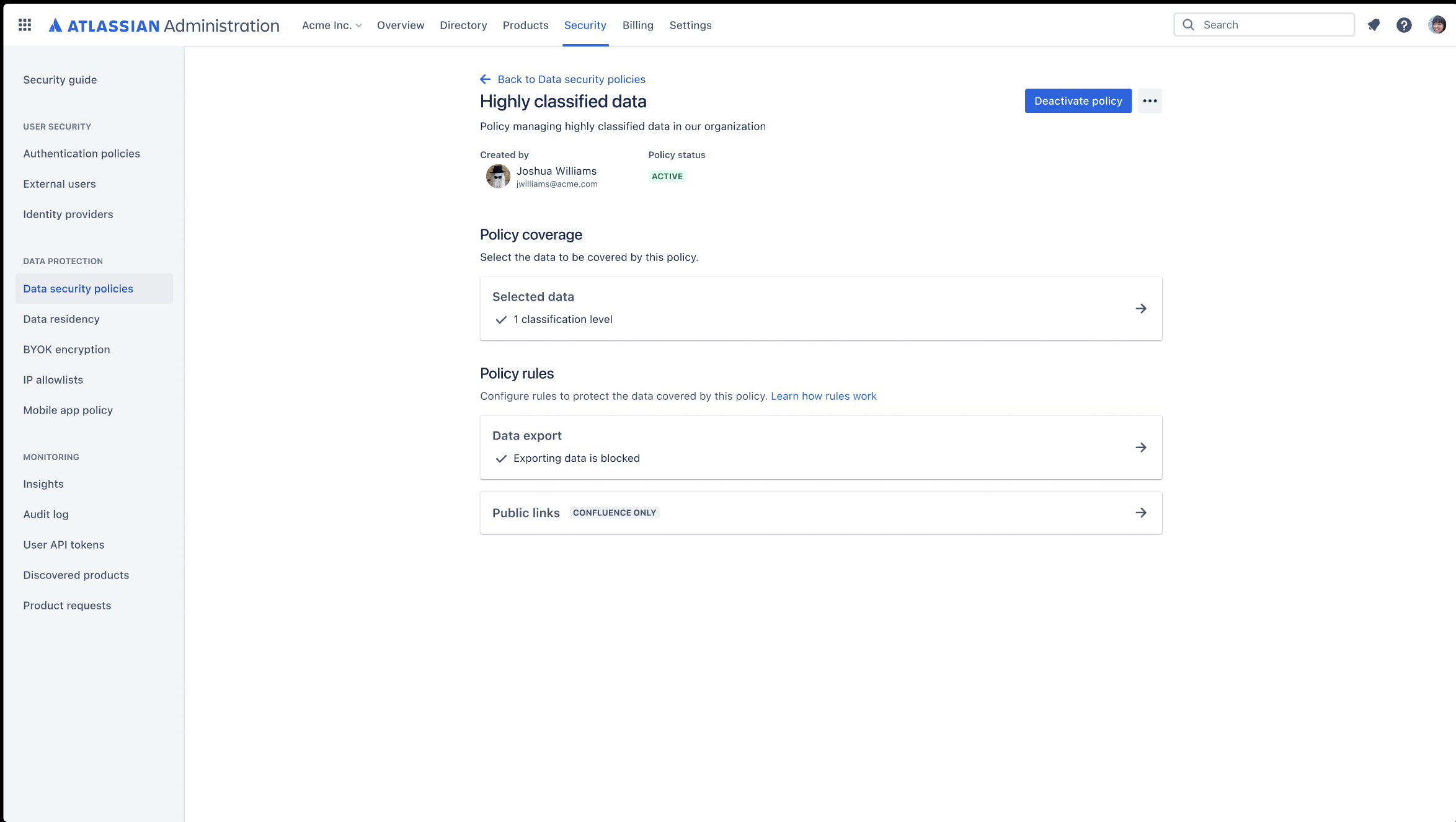
Use data classification levels as a coverage in your data security policy. Create policies to govern how users, apps, and people outside of your organization can interact with content such as Confluence pages and Jira issues.
Use data classification to set additional rules within your data security policy, including: "Block Export" rule in Confluence and Jira, “Anonymous Access” rule in Jira, and “Block Public Links” rule in Confluence using classification.
Automatic product discovery
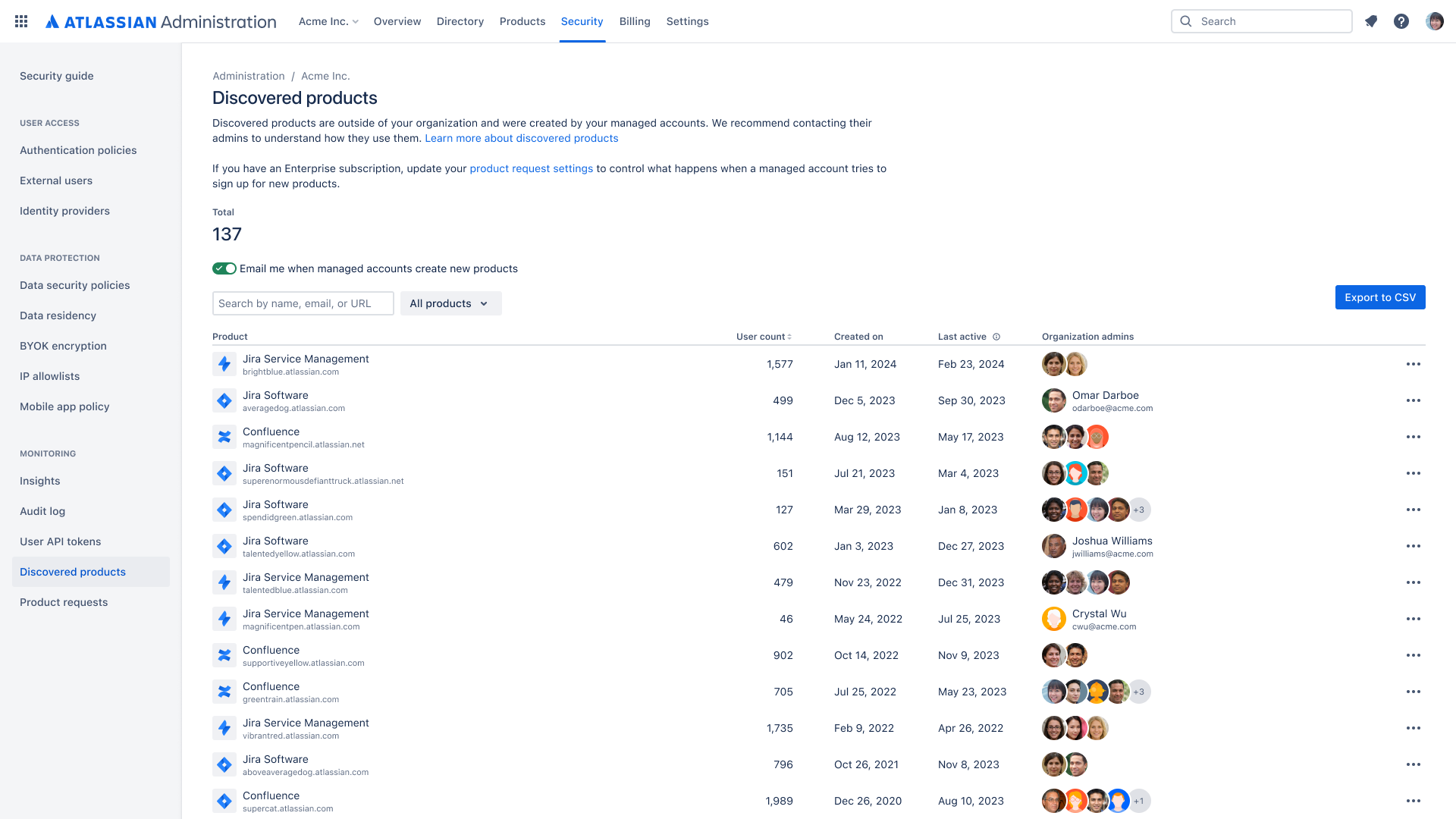
Gain visibility into shadow IT by discovering when managed users in your organization create instances across Atlassian cloud products. Automatic product discovery identifies the product administrator and how many users are using these products.
Organization insights
Admins can achieve better visibility into the usage of their Atlassian products and make more data-driven decisions when it comes to increasing adoption or optimizing their products' ROI.
Organization audit log: Admin activity
79b0.png)
A centralized log of admin activity across your Atlassian cloud organization. Gain a full view of the who, what, and when of admin activity to help track and identify any suspicious behavior. Using APIs, integrate with your third party tools, such as a CASB.
Comprehensive organization audit log: User activity, API tokens, Webhooks
79b0.png)
A comprehensive log of org admin, product admin, and user activity that takes place in the Atlassian cloud organization. This provides organization admins with visibility into activities like which managed users have created an API token or what organizational resources are being accessed by managed and external users via API tokens. Audit log webhooks are customized HTTP callbacks that trigger in response to audit log events.
Anomalous activity detections
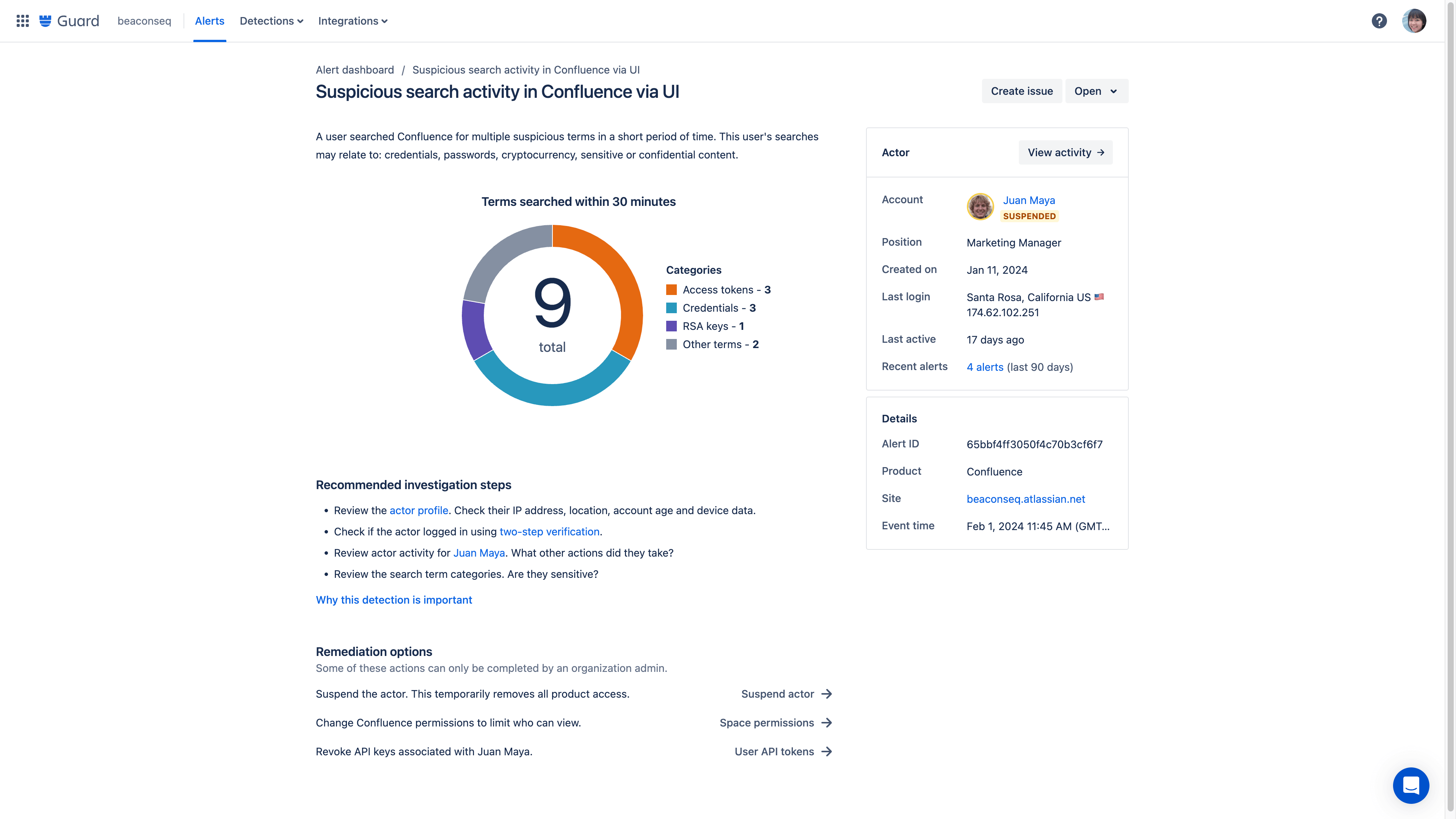
Anomalous activity detections provide intelligent oversight across your Atlassian cloud products by analyzing user activity and notifying you of potential risks. These queries search activity logs and alert you to any potentially concerning activity that requires review.
Content scanning
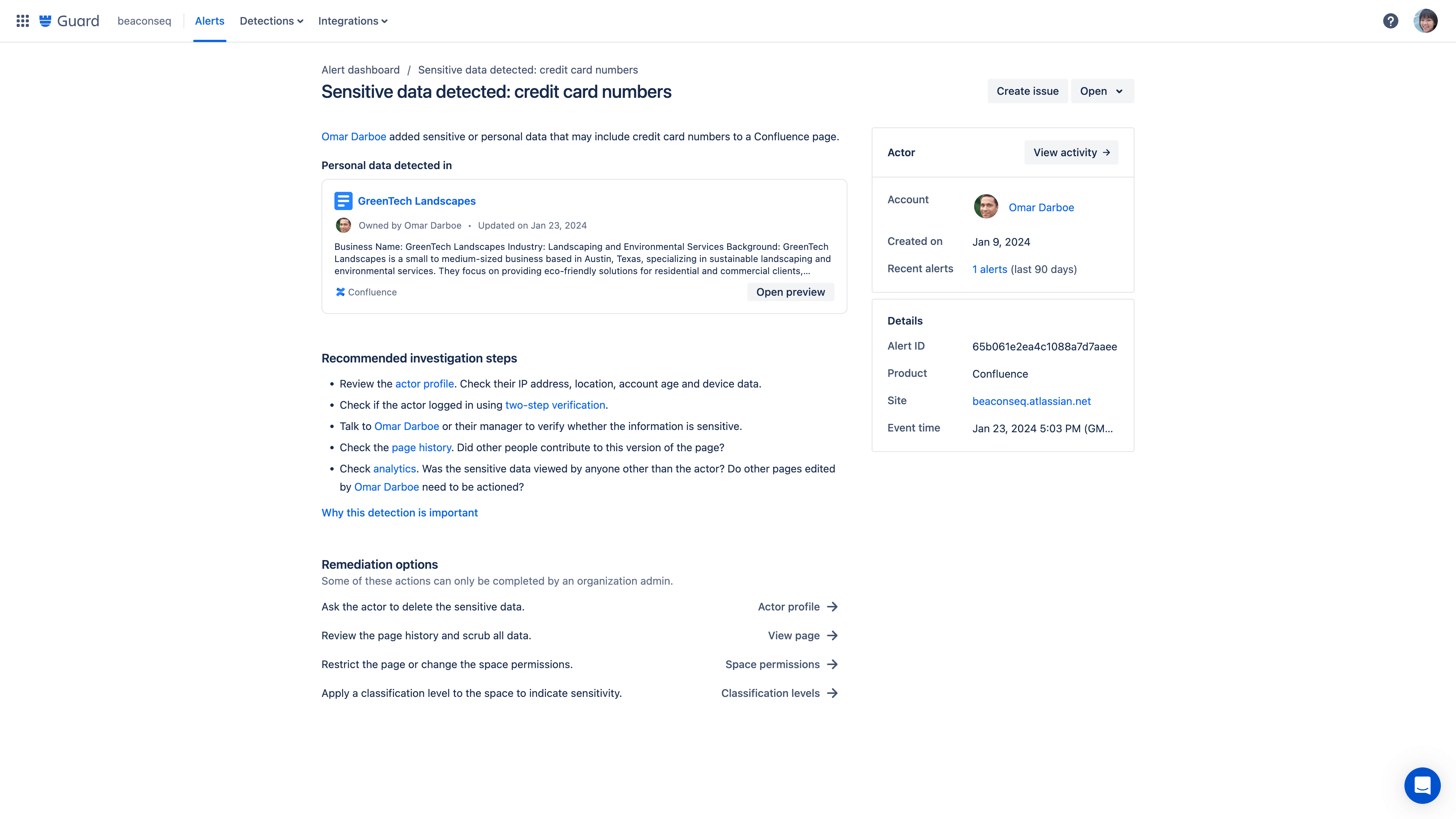
Content scanning detection rules monitor for critical data being added to Confluence pages. These detections generate alerts for any potentially concerning content that requires review.
SIEM integrations
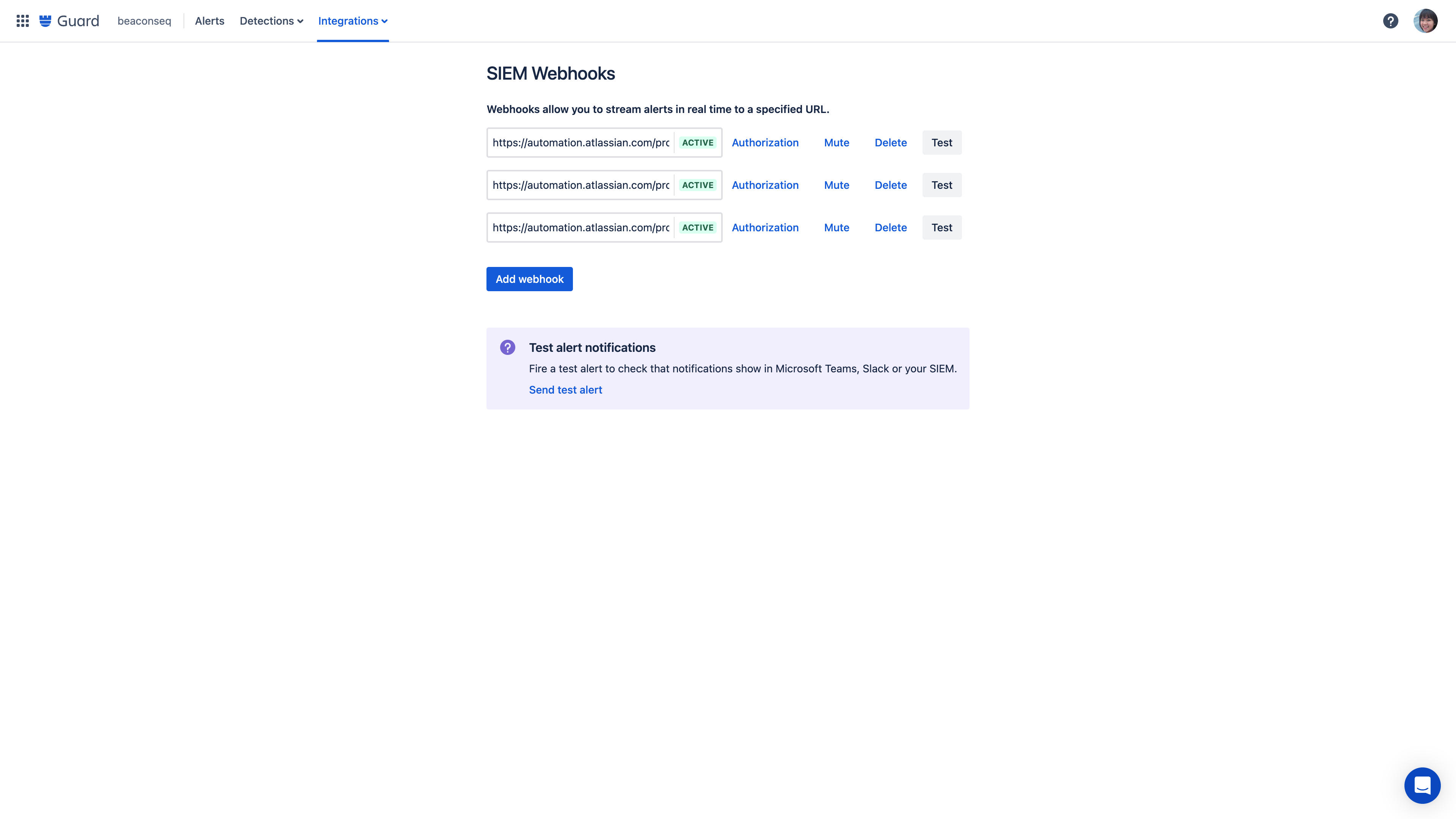
Using webhooks, send alerts about anomalous activity to any destination, including your organization-wide SIEM or an automation tool like Jira Automation, Zapier, or Workato.
Alert messaging integrations
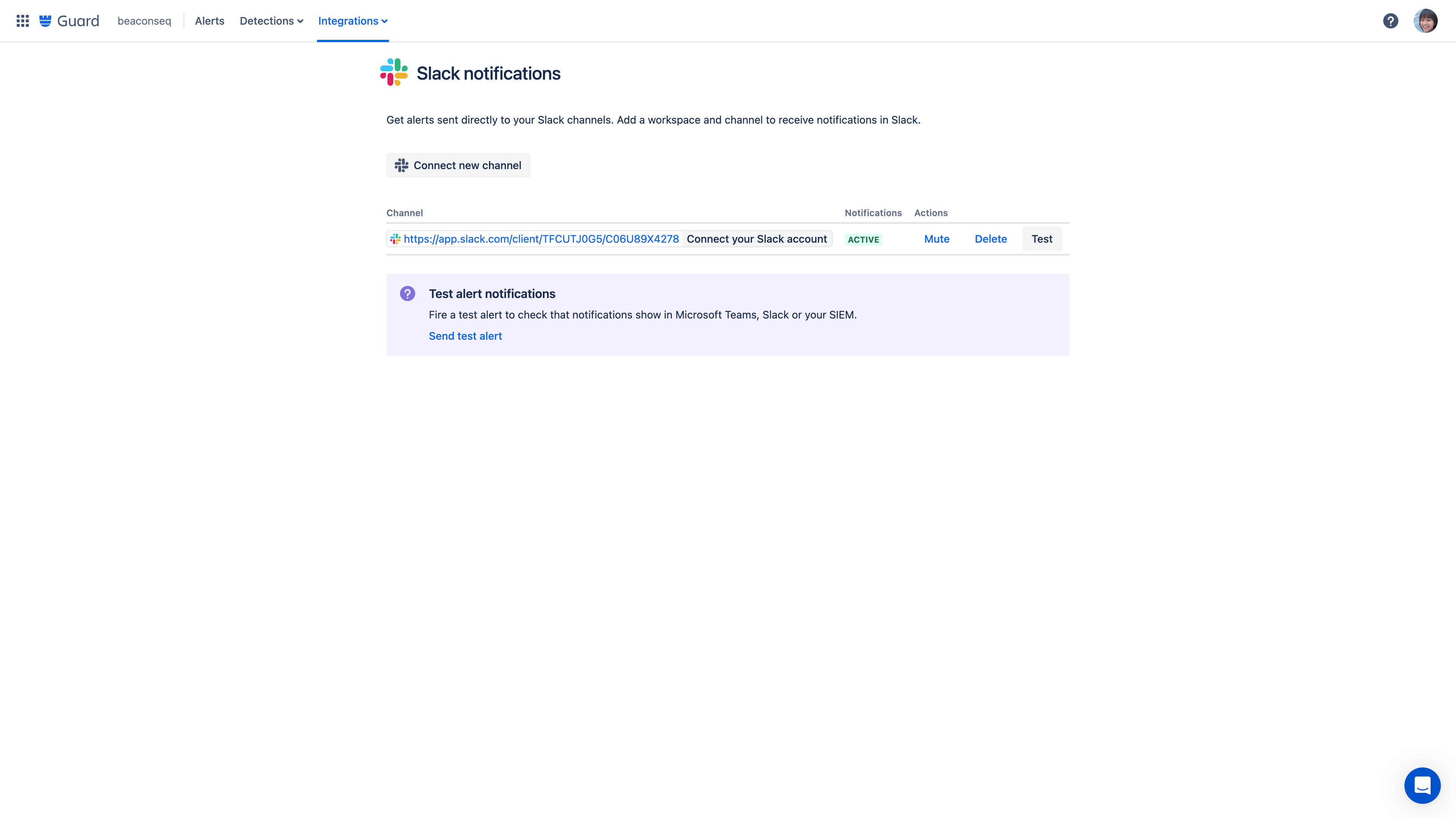
Integrate alert messages to your organization-wide tools like Slack, Microsoft Teams, and more.
Alert investigations
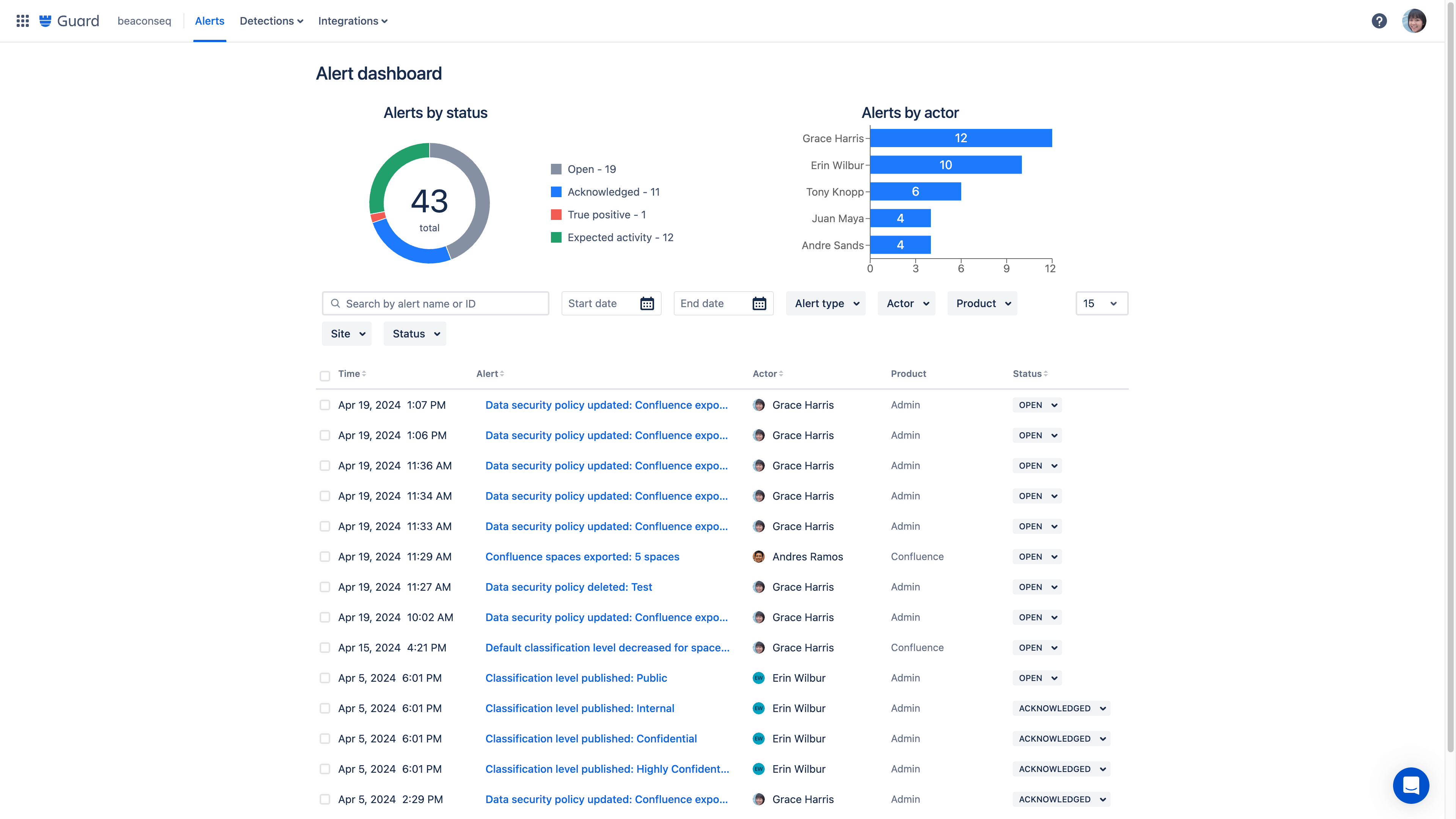
Alert investigations gives admins or security teams a consolidated view of potentially risky activity. Investigate the alert with details on what happened, which account was involved, other recent alerts tied to this account, and remediation options.
Actor profiles
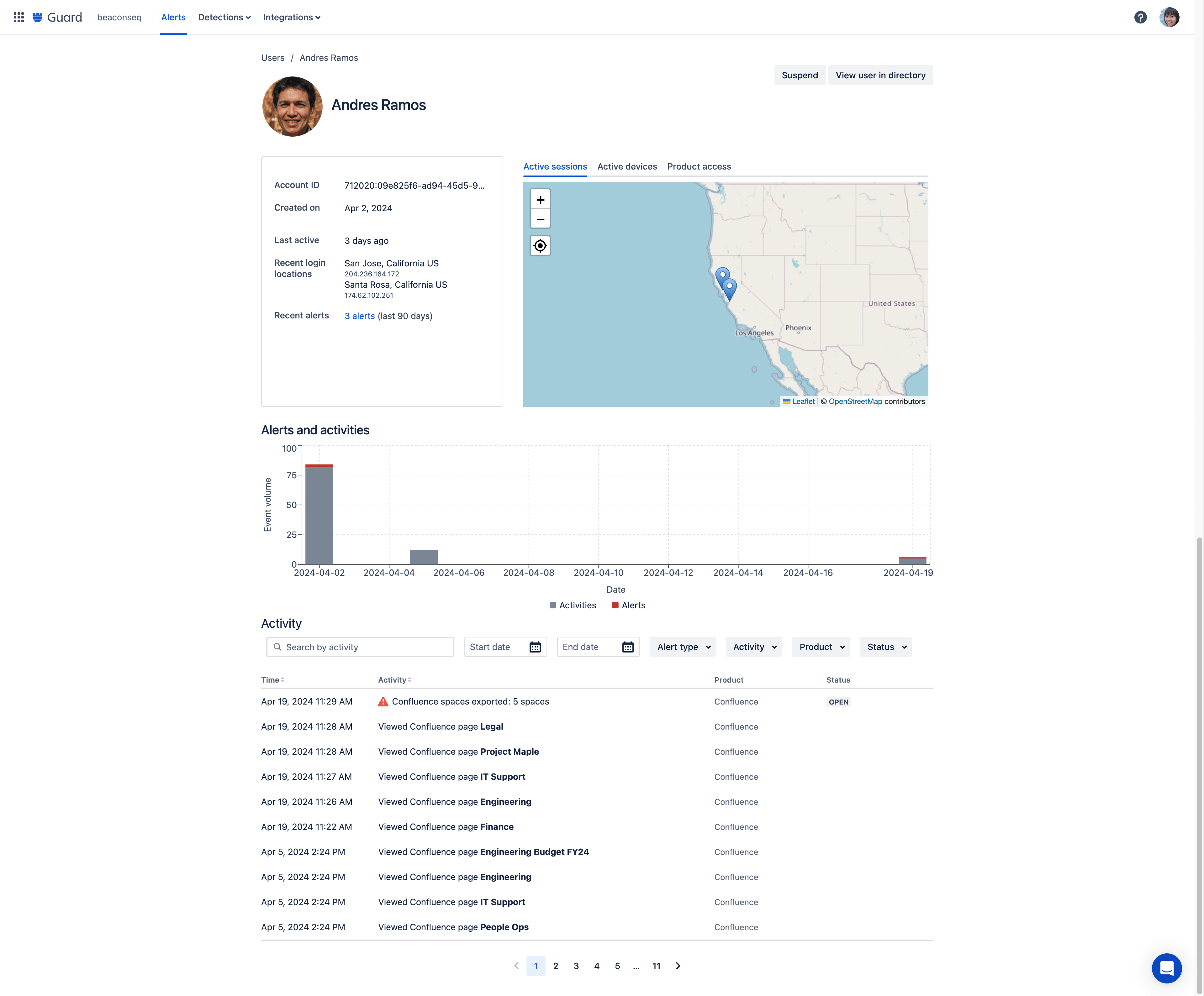
Access detailed user data by clicking into an actor profile directly from an alert to see a consolidated view of a user’s activity. On a single page, you can see a user’s role, location, recent activity, and a full list of their audit log alerts.
Remediation workflows

If suspicious behavior is detected, an organization admin can take action using the remediation recommendation to follow the suggested workflow and address a threat. Admins have the ability to immediately suspend a user's account directly from the alert dashboard.
Remediation recommendations
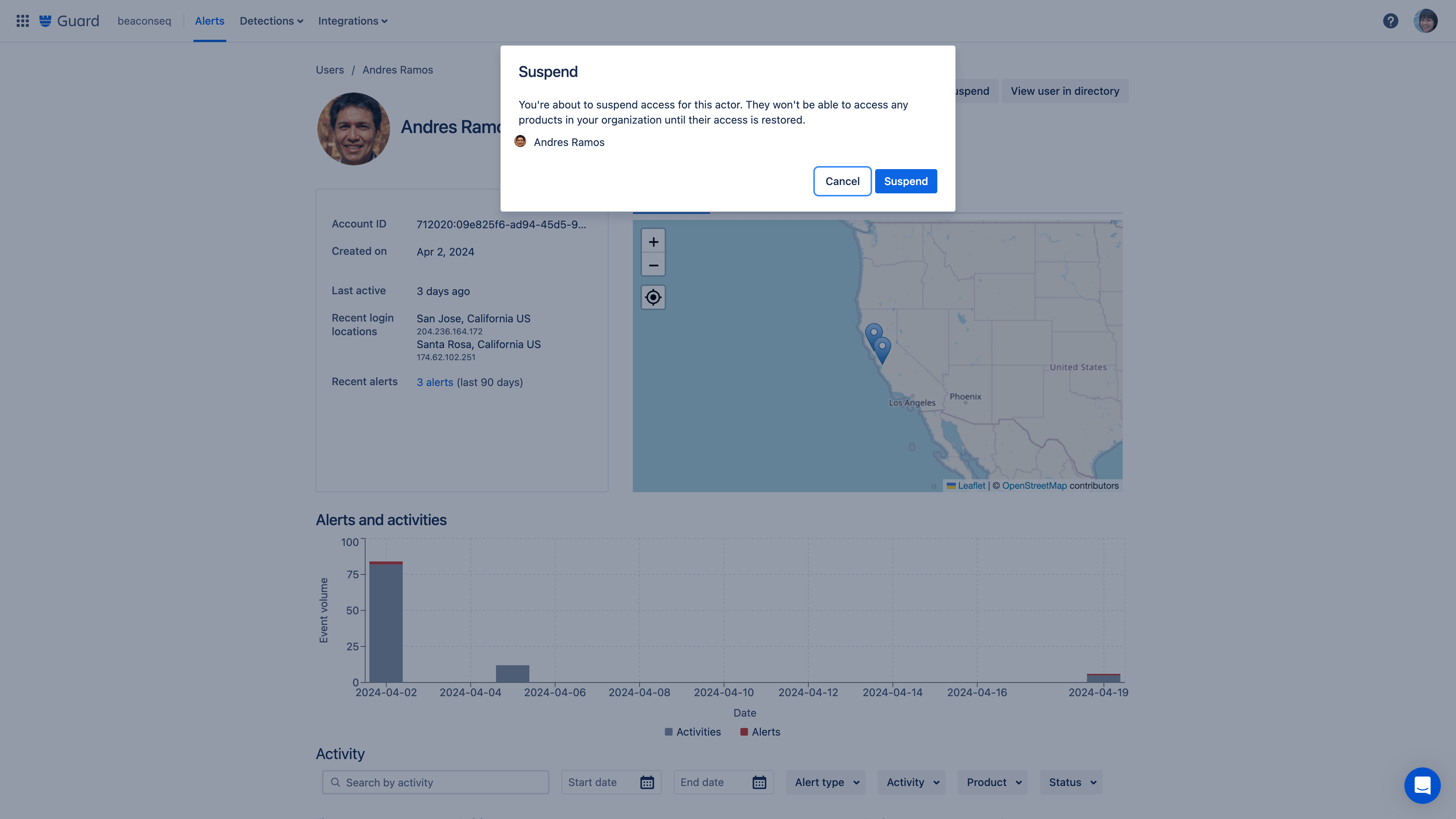
Respond to alerts faster with the ability to suspend a user’s account directly from the alert dashboard. Based on the actions logged in the dashboard, remediation options are recommended with actionable next steps.
Alert hand-off
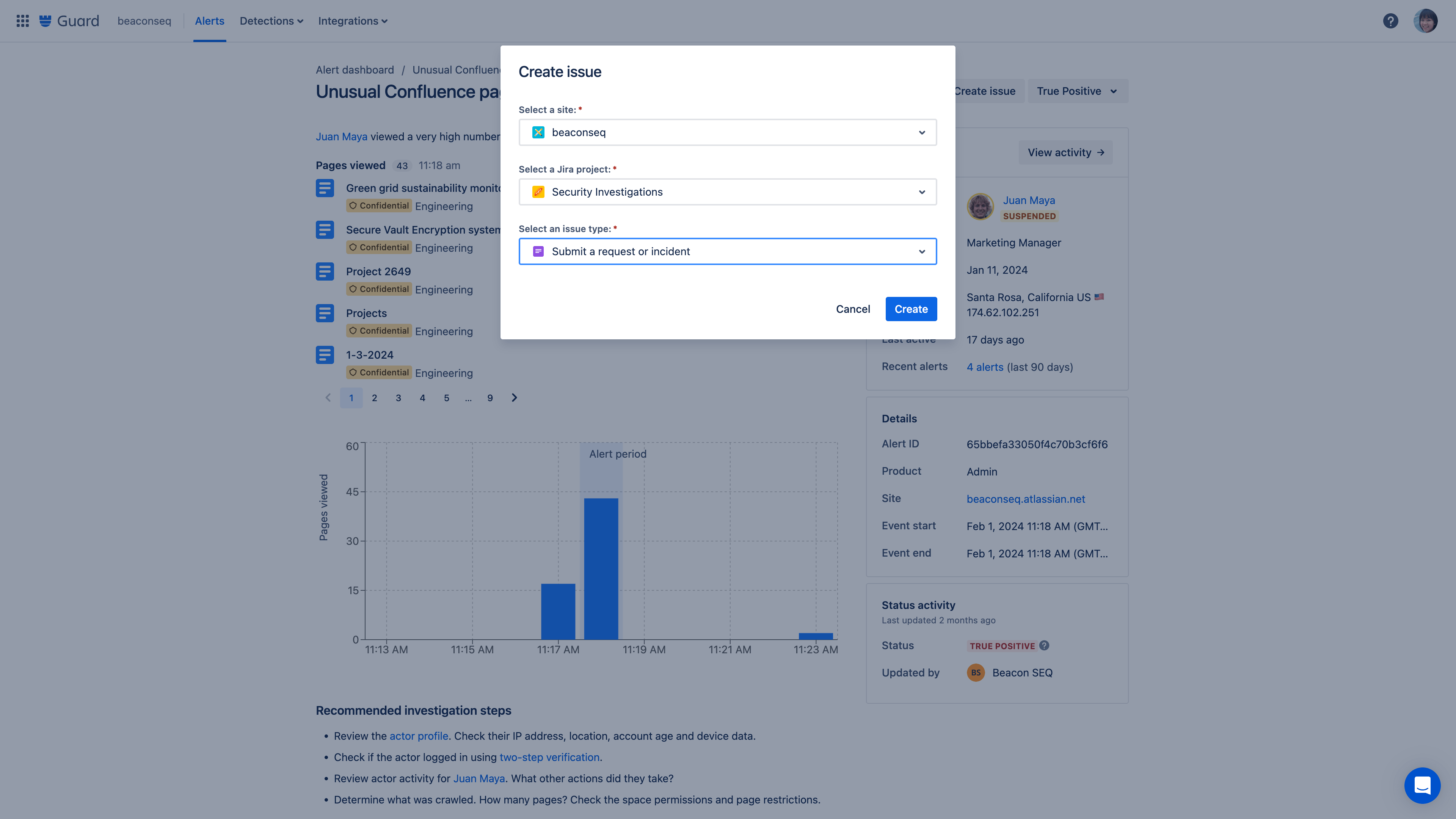
Connect an alert to Jira through the create issue button.
Questions about Atlassian Guard billing?
Visit our billing and licensing page for details.
Enforced two-step verification
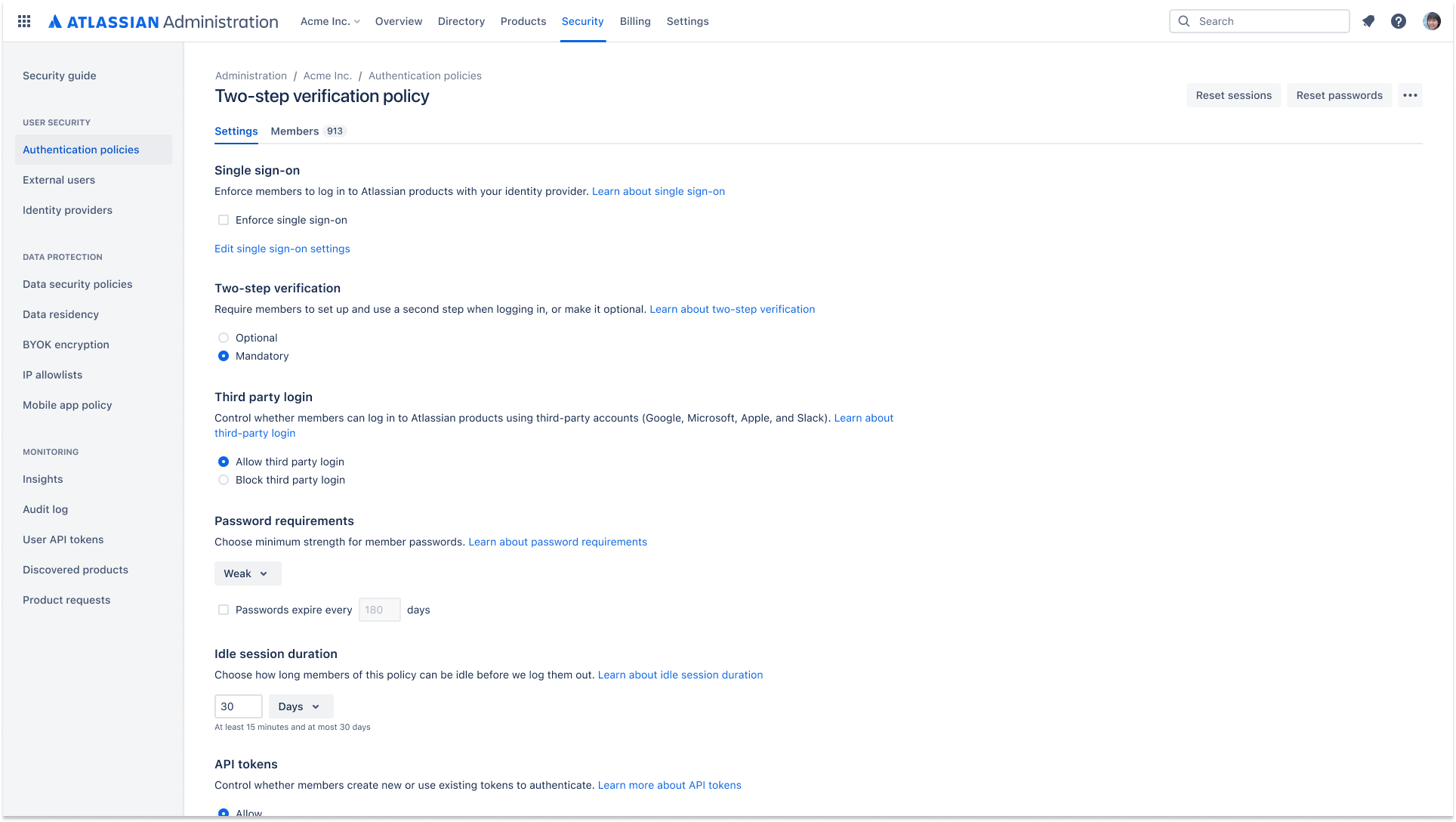
Enforced two-step verification can be applied as part of an authentication policy. This requires the users in an organization to turn on two-step verification in order to log in and access their Atlassian cloud products.