30일 무료 평가 기간
기능 비교
| Standard | Premium | |
| Protect against data loss proactively | ||
| Feature | Standard | Premium |
| Enforced single sign-on (SSO) ? | Standard ✓ | Premium ✓ |
| SCIM automated user provisioning ? | Standard ✓ | Premium ✓ |
| Authentication policies ? | Standard ✓ | Premium ✓ |
| External user security ? | Standard ✓ | Premium ✓ |
| Enforced two-step verification ? | Standard ✓ | Premium ✓ |
| Mobile app management (MAM) ? | Standard ✓ | Premium ✓ |
| API token controls ? | Standard ✓ | Premium ✓ |
| Data security policies ? | Standard ✓ | Premium ✓ |
| Data classification ? | Standard - | Premium ✓ |
| Enforce data security policies by classification ? | Standard - | Premium ✓ |
| Detect and investigate suspicious activity | ||
| Feature | Standard | Premium |
| Automatic product discovery ? | Standard ✓ | Premium ✓ |
| Organization insights ? | Standard ✓ | Premium ✓ |
| Organization audit log: Admin activity ? | Standard ✓ | Premium ✓ |
| Comprehensive organization audit log: User activity, API tokens, Webhooks ? | Standard - | Premium ✓ |
| Anomalous activity detections ? | Standard - | Premium ✓ |
| Content scanning ? | Standard - | Premium ✓ |
| SIEM integrations ? | Standard - | Premium ✓ |
| Alert messaging integrations ? | Standard - | Premium ✓ |
| Respond to threats before they become incidents | ||
| Feature | Standard | Premium |
| Alert investigations ? | Standard - | Premium ✓ |
| Actor profiles ? | Standard - | Premium ✓ |
| Remediation recommendations ? | Standard - | Premium ✓ |
| Remediation workflows ? | Standard - | Premium ✓ |
| Alert hand-off ? | Standard - | Premium ✓ |
See Atlassian Guard in action
Atlassian Access 기능
| 관리되는 모든 사용자가 기존 ID 공급자를 통해 Atlassian Cloud 제품에 인증할 수 있도록 하려면 SSO(Single Sign-On)를 적용하세요. 즉, 사용자는 단순히 사용자 이름 및 비밀번호가 아닌 더 안전한 인증 방법을 통해 동일한 자격 증명으로 여러 도구에 액세스할 수 있습니다. |
| SCIM 프로비전 및 프로비전 해제를 통해 사용자 수명 주기 관리를 자동화하세요. Atlassian Cloud 제품에 대한 액세스 권한은 외부 디렉터리에 설정된 규칙에 의해 정의됩니다. 사용자 프로비저닝은 직원이 회사에 입사하거나 새로운 팀으로 이동할 때 이들에게 애플리케이션 액세스 권한을 부여하는 데 필요한 수동 작업을 줄여 줍니다. |
| 관리자는 인증 정책을 설정하여 세션 기간, SSO(Single Sign-On), 비밀번호 정책 및 2단계 인증을 관리할 수 있습니다. 여러 정책을 만들어 관리 계정의 다른 하위 집합에 적용할 수 있습니다. |
| 2단계 인증을 인증 정책의 일부로 적용할 수 있습니다. 이렇게 하려면 조직의 사용자가 로그인하고 Atlassian Cloud 제품에 액세스할 때 2단계 인증을 활성화해야 합니다. |
| 모바일 앱 관리(MAM)로 관리되는 사용자 및 관리되지 않는 사용자 모두에 적용할 수 있는 보안 정책을 만들고 관리하세요. 정책은 조직 수준에서 설정하거나 일부 사용자에 대해 스크린샷 사용 중지, 데이터 내보내기 제한 및 기기 암호화 요구 사항과 같은 추가 보안 컨트롤을 제공하도록 지정할 수 있습니다. |
| 조직의 관리되는 사용자가 Atlassian Cloud 제품에서 인스턴스를 만들 때 발견하여 섀도우 IT에 대한 가시성을 확보하세요. 자동 제품 탐색으로 제품 관리자 및 해당 제품을 사용하는 사용자 수를 파악하세요. |
| Atlassian Cloud 조직에서 일어나는 관리자 활동의 종합적 로그입니다. 조직 감사 로그를 통해 관리자는 누가, 언제, 어떤 관리자 활동을 실행했는지 확인하여 조직이 의심스러운 행동을 추적 및 파악할 수 있습니다. |
| Atlassian Access를 CASB에 통합하여 Atlassian의 로그인 및 관리 활동의 전체 기록을 캡처하세요. 사용자 자격 증명 손상, 잘못된 비밀번호 보호 또는 지나치게 많은 권한이 부여된 계정으로 인한 내부자 위협과 같은 일반적인 위협으로부터 방어하세요. McAfee MVISION 또는 Microsoft Defender CASB 연결에 대해 자세히 알아보세요. |
Enforced single sign-on (SSO)
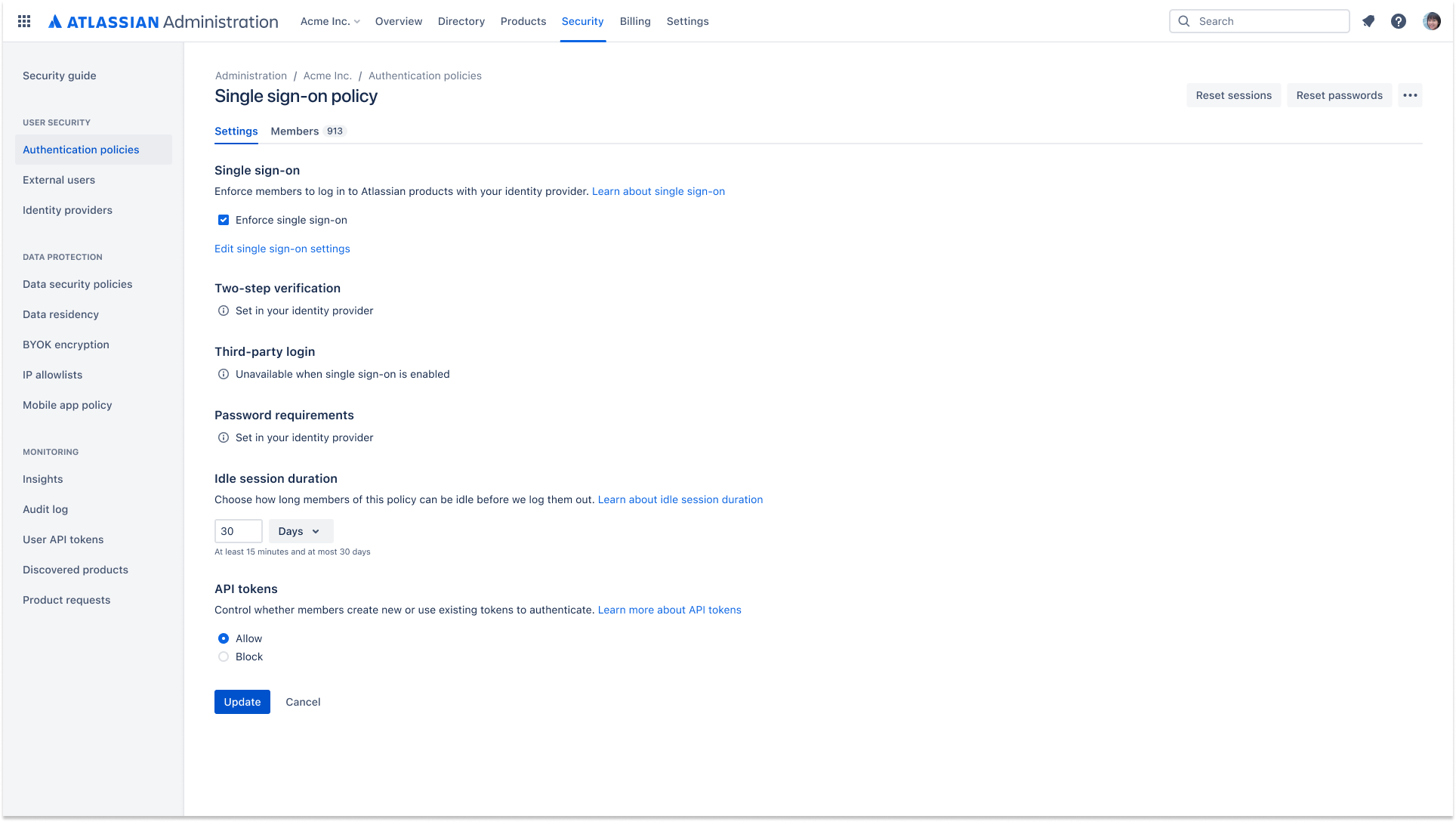
참고: 이 표에는 간단하게 확인할 수 있도록 사용자 수가 5,000명까지만 표시되어 있습니다. Access는 사용자 수에 제한이 없습니다. 사용자 수가 5,000명을 초과하는 경우 가격 계산기를 사용하여 연간 가격을 확인할 수 있습니다.
SCIM automated user provisioning
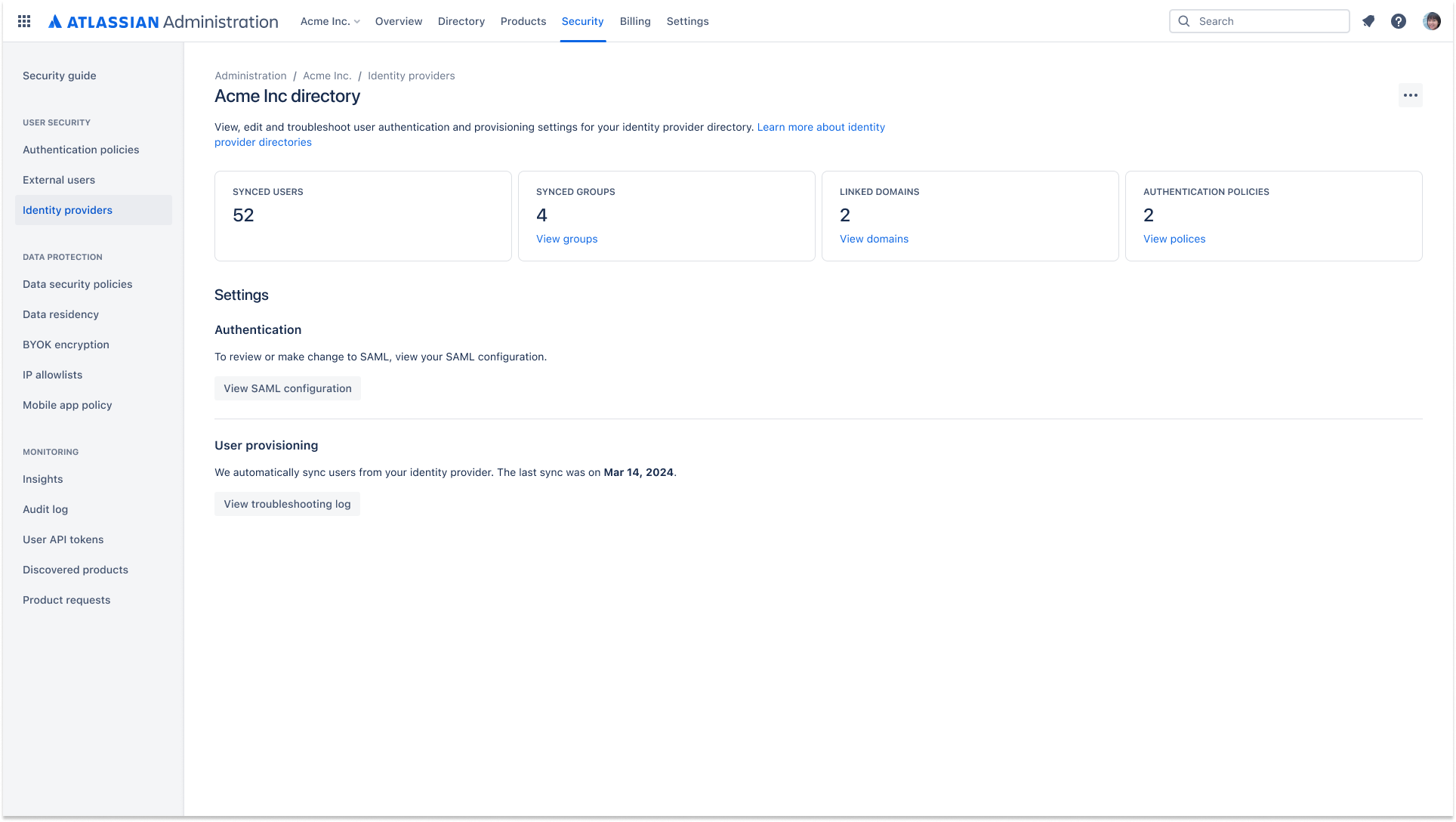
Automate user lifecycle management with SCIM provisioning and de-provisioning. Access to Atlassian cloud products will be defined by rules set in your external directory.
Authentication policies
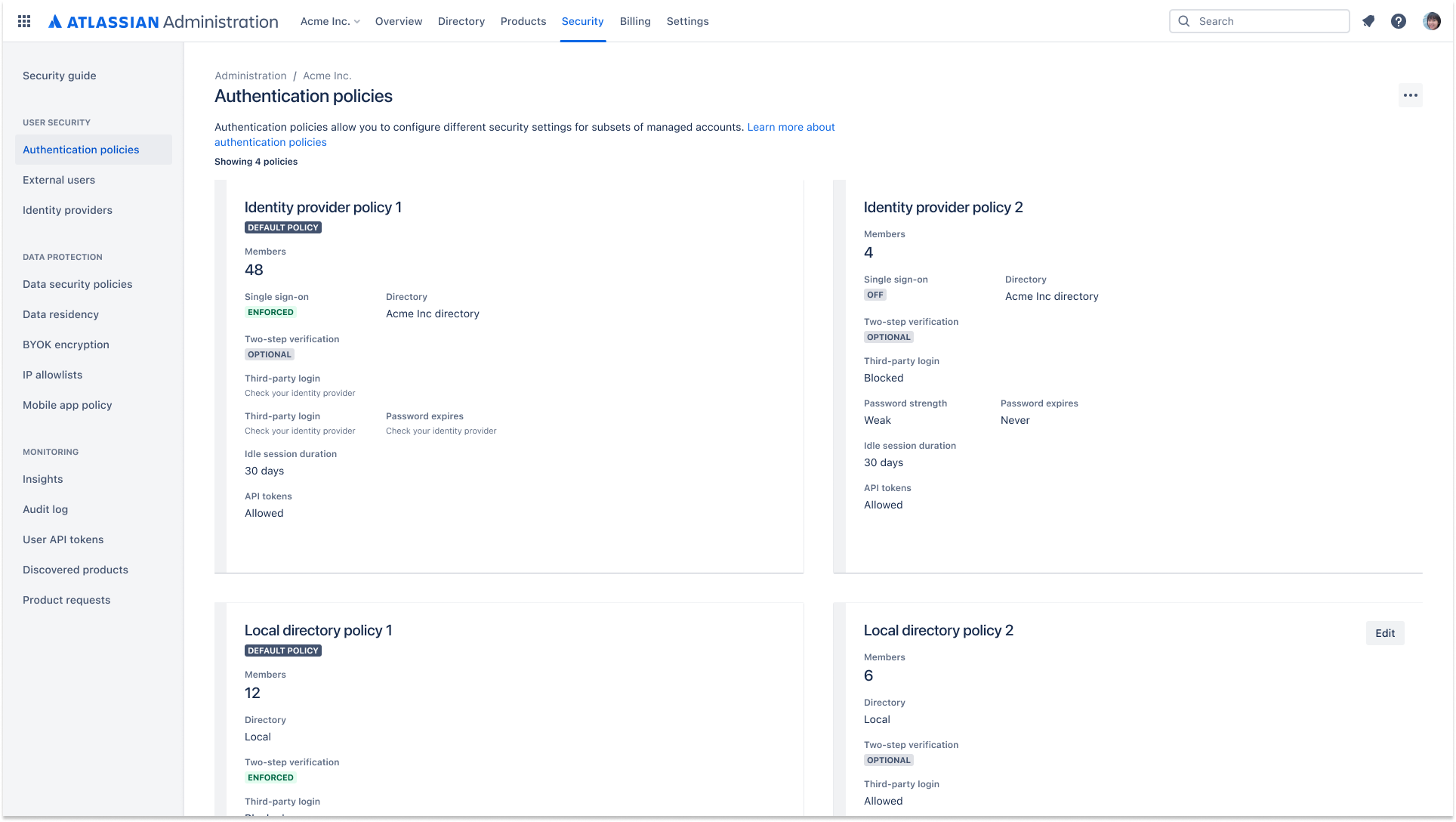
Admins can set authentication policies to manage session duration, single sign-on (SSO), password policies, and two-step verification. Multiple policies can be created and applied to different subsets of managed accounts.
External user security
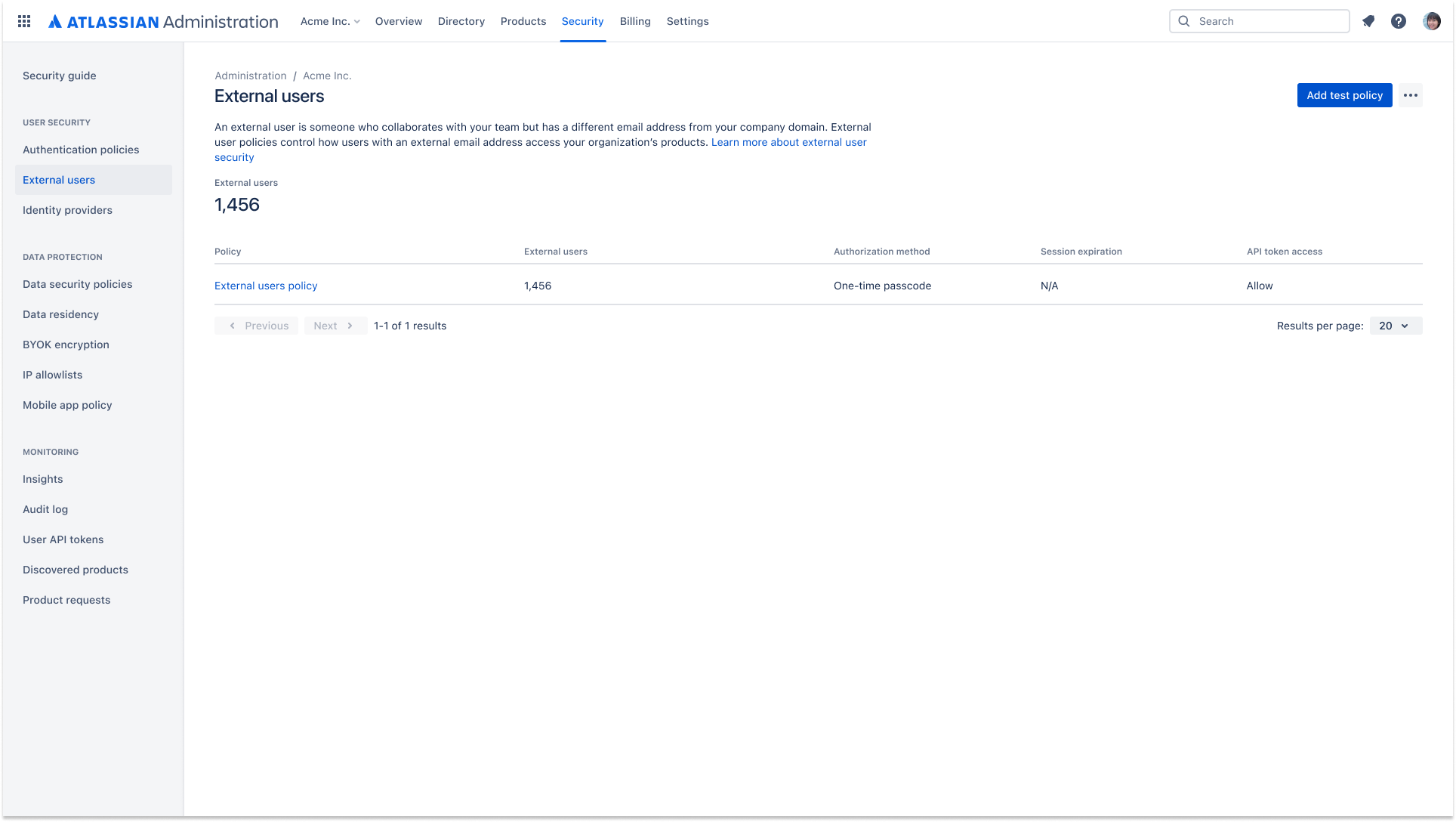
An external user policy allows you to apply security settings, including two-step verification, to external users. The settings apply to all the external users in your Atlassian organization.
Mobile app management (MAM)
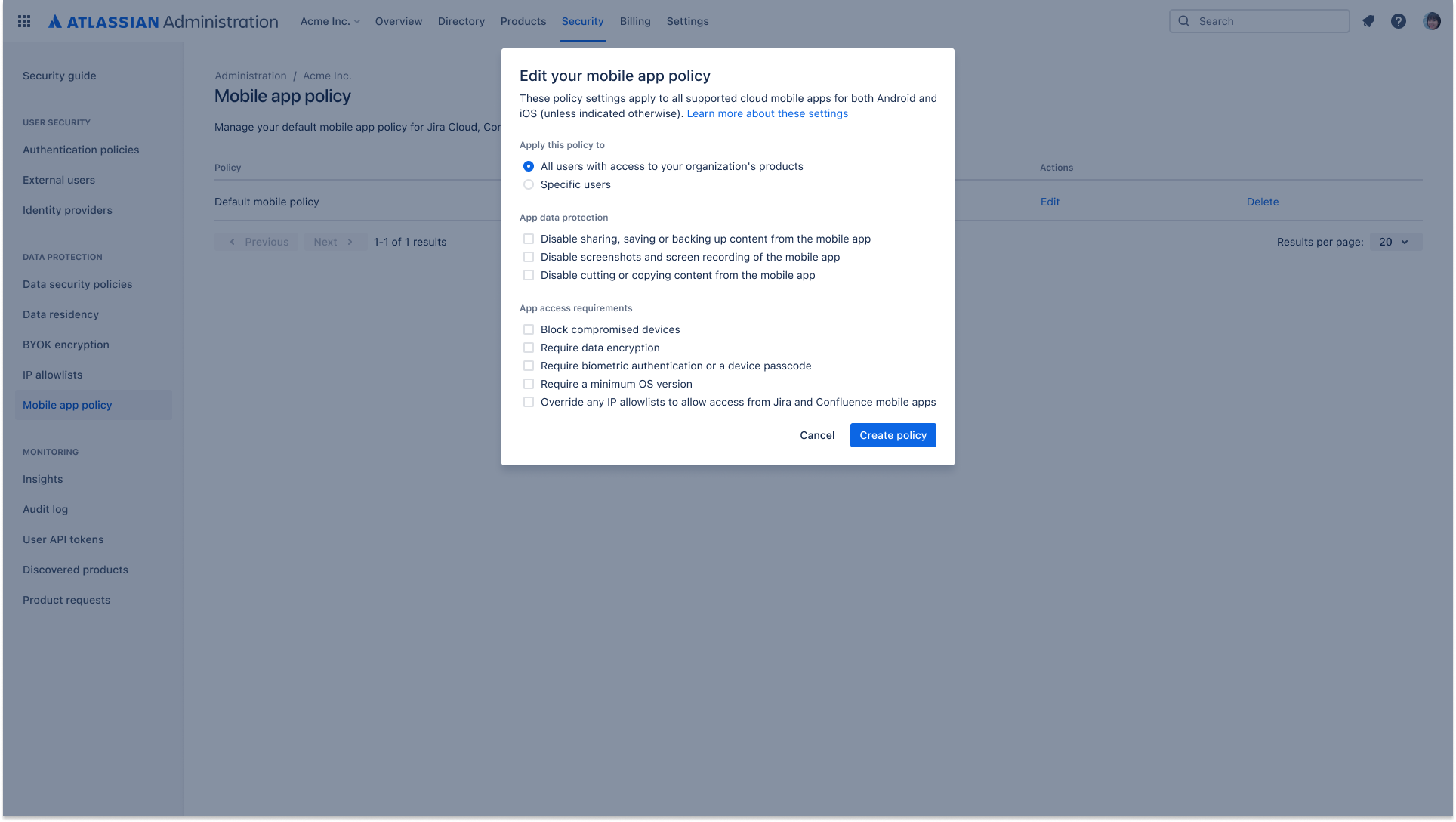
Create and manage security policies that can be applied to both managed and unmanaged users with mobile app management (MAM). Policies can be set at the organization level, or designated for select users to provide additional security controls such as screenshot disabling, data export restrictions and device encryption requirements
API token controls
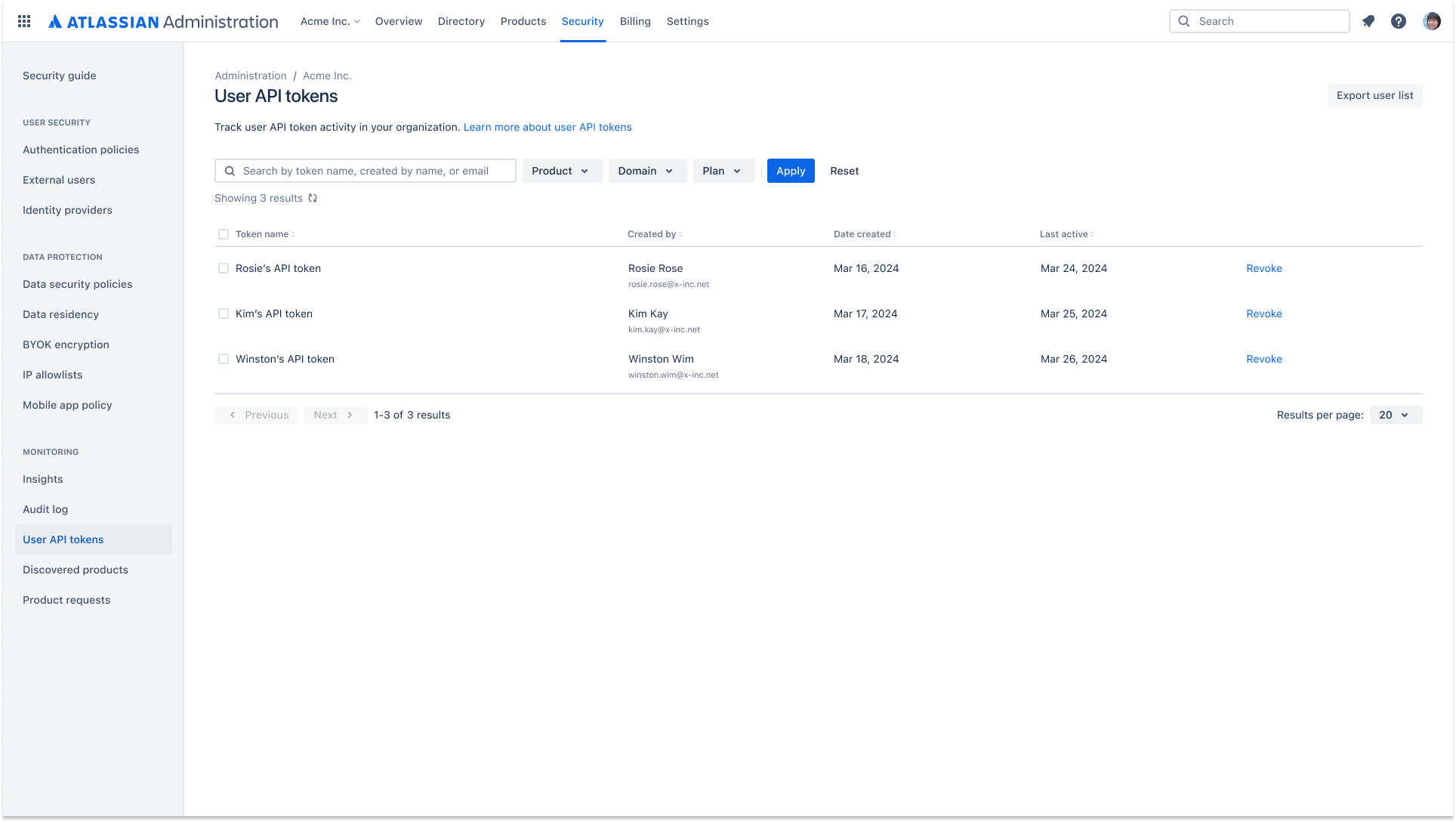
Admins have greater visibility and control over API token management and its lifecycle. This includes controlling which users can create an API token to access data and viewing which users are creating and revoking API tokens.
Data security policies
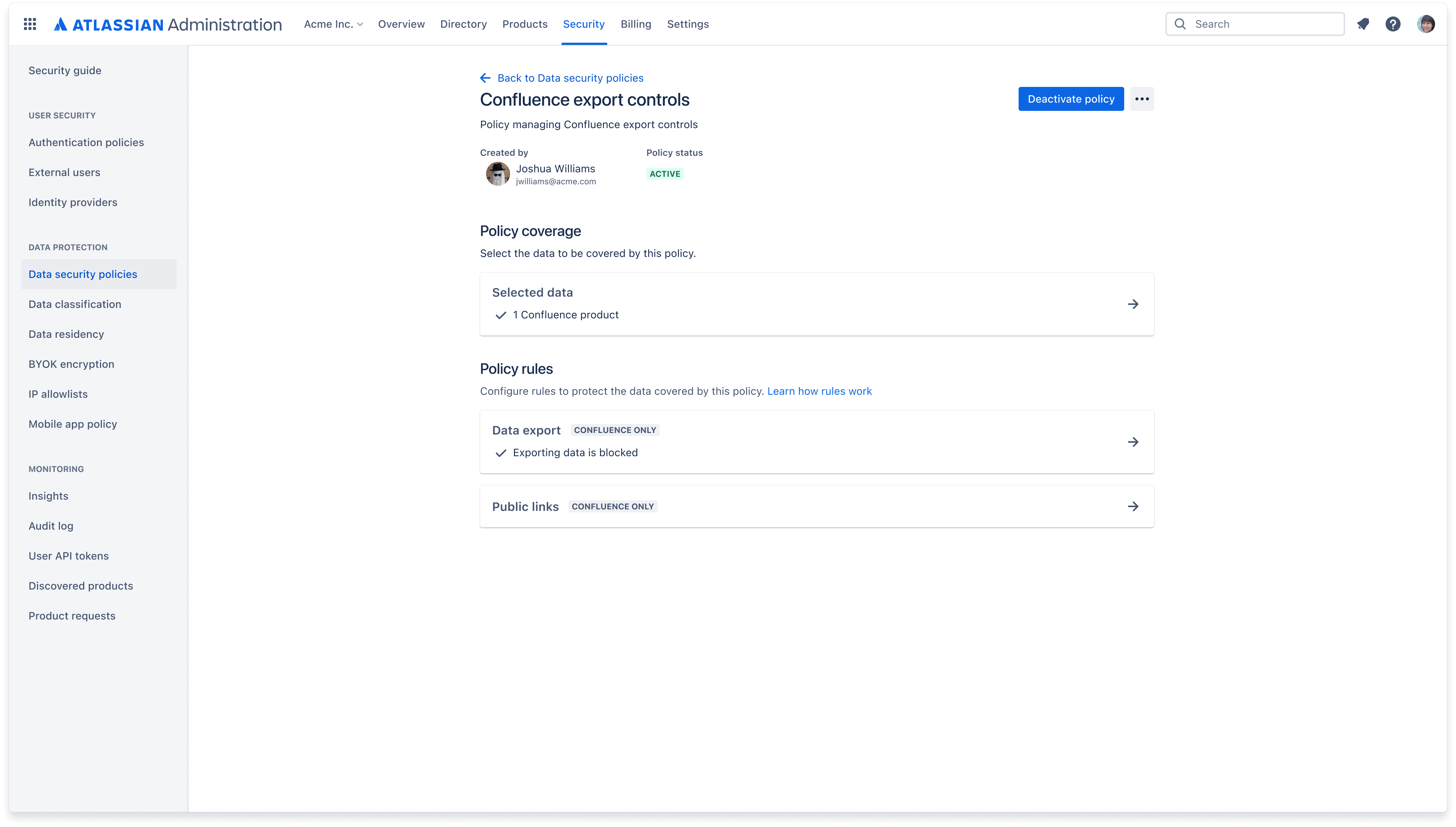
A data security policy helps you keep your organization’s data secure. Create policies to govern how users, apps, and people outside of your organization can interact with content such as Confluence pages and Jira issues.
Data classification
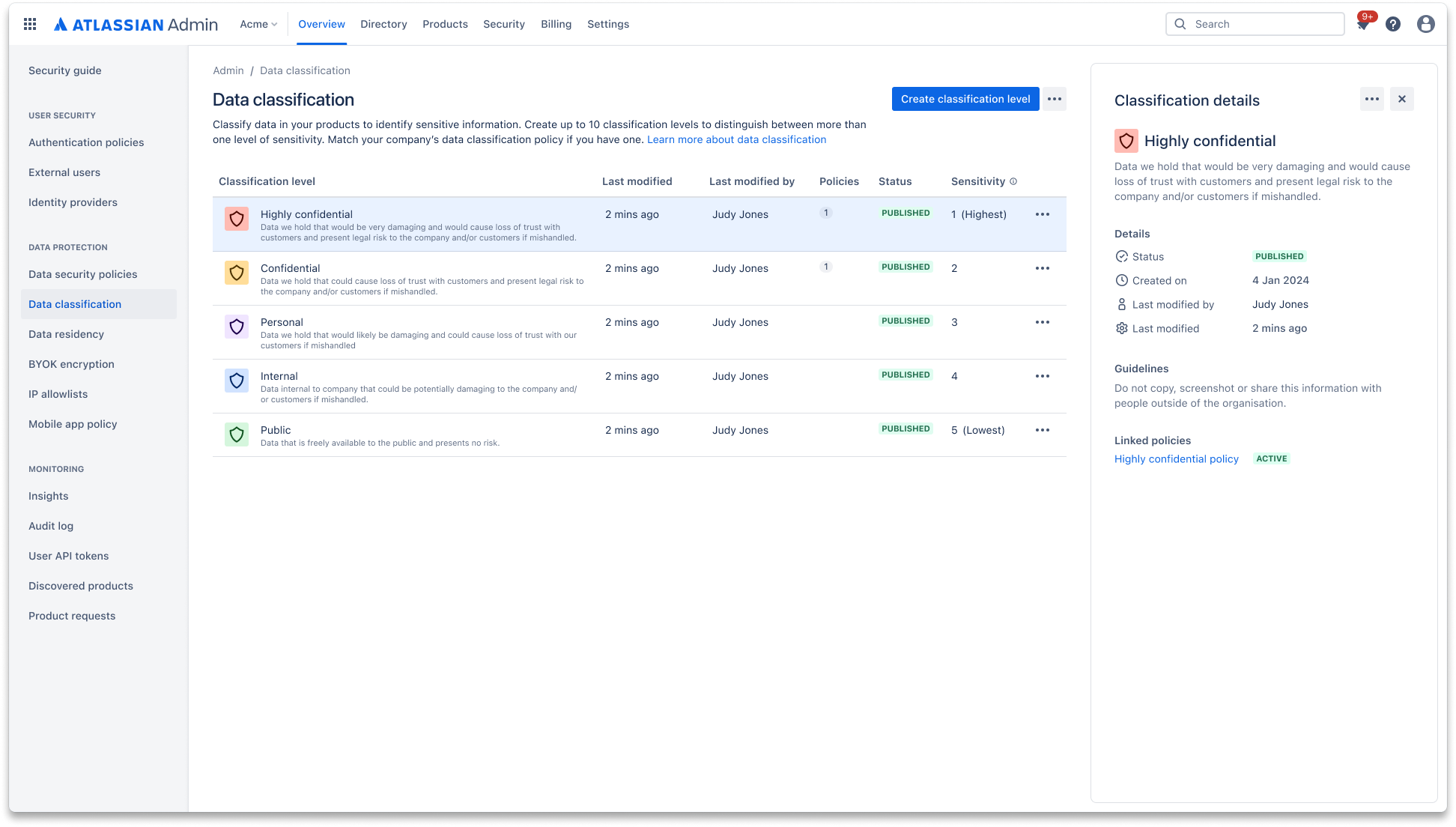
Data classification allows admins to define their data governance approach and label critical data accordingly within Atlassian products. Admins can set data security policies and rules to control user interaction based on data classification level.
Enforce data security policies by classification
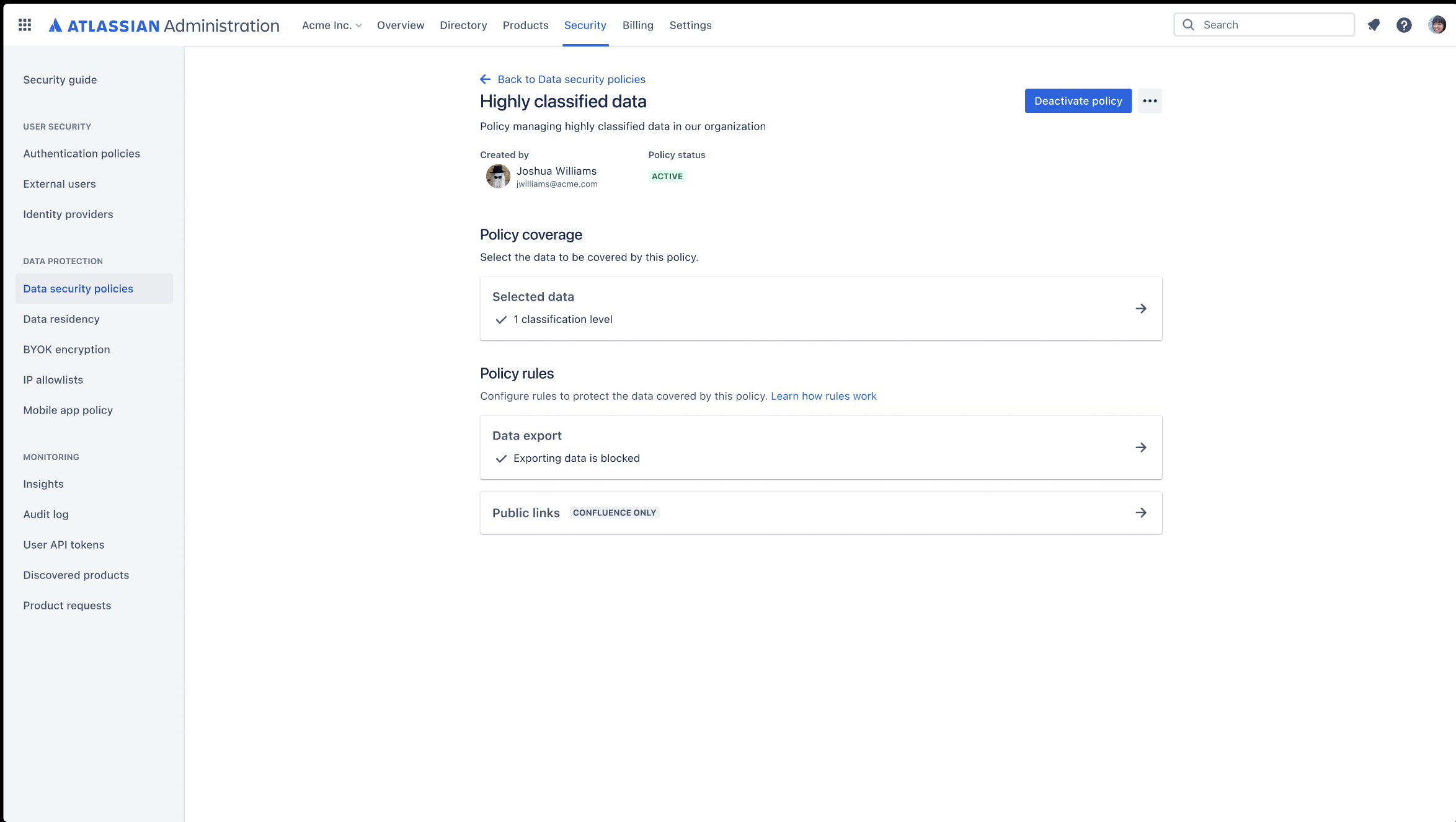
Use data classification levels as a coverage in your data security policy. Create policies to govern how users, apps, and people outside of your organization can interact with content such as Confluence pages and Jira issues.
Use data classification to set additional rules within your data security policy, including: "Block Export" rule in Confluence and Jira, “Anonymous Access” rule in Jira, and “Block Public Links” rule in Confluence using classification.
Automatic product discovery
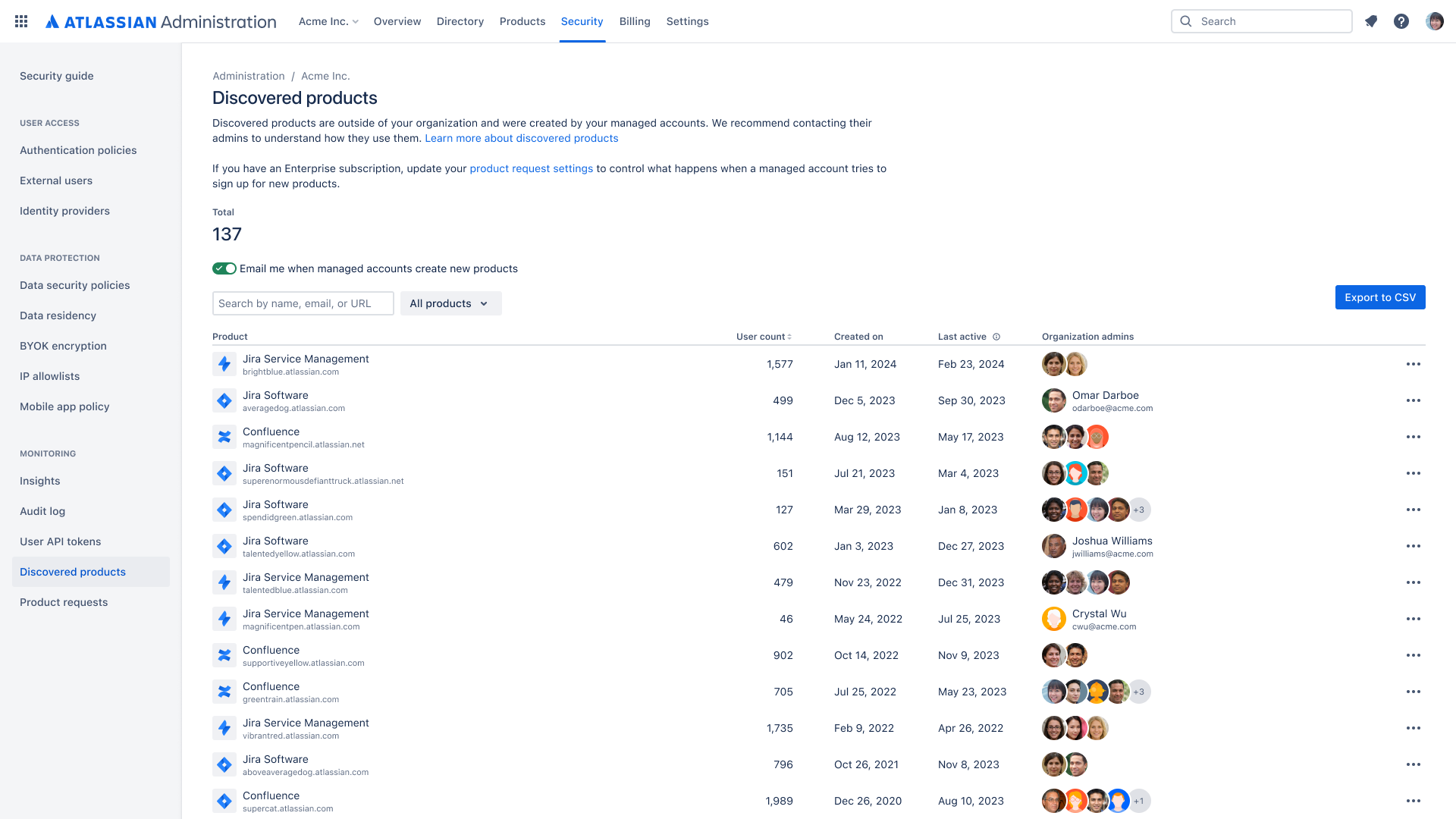
Gain visibility into shadow IT by discovering when managed users in your organization create instances across Atlassian cloud products. Automatic product discovery identifies the product administrator and how many users are using these products.
Organization insights
Admins can achieve better visibility into the usage of their Atlassian products and make more data-driven decisions when it comes to increasing adoption or optimizing their products' ROI.
Organization audit log: Admin activity
79b0.png)
A centralized log of admin activity across your Atlassian cloud organization. Gain a full view of the who, what, and when of admin activity to help track and identify any suspicious behavior. Using APIs, integrate with your third party tools, such as a CASB.
Comprehensive organization audit log: User activity, API tokens, Webhooks
79b0.png)
A comprehensive log of org admin, product admin, and user activity that takes place in the Atlassian cloud organization. This provides organization admins with visibility into activities like which managed users have created an API token or what organizational resources are being accessed by managed and external users via API tokens. Audit log webhooks are customized HTTP callbacks that trigger in response to audit log events.
Anomalous activity detections
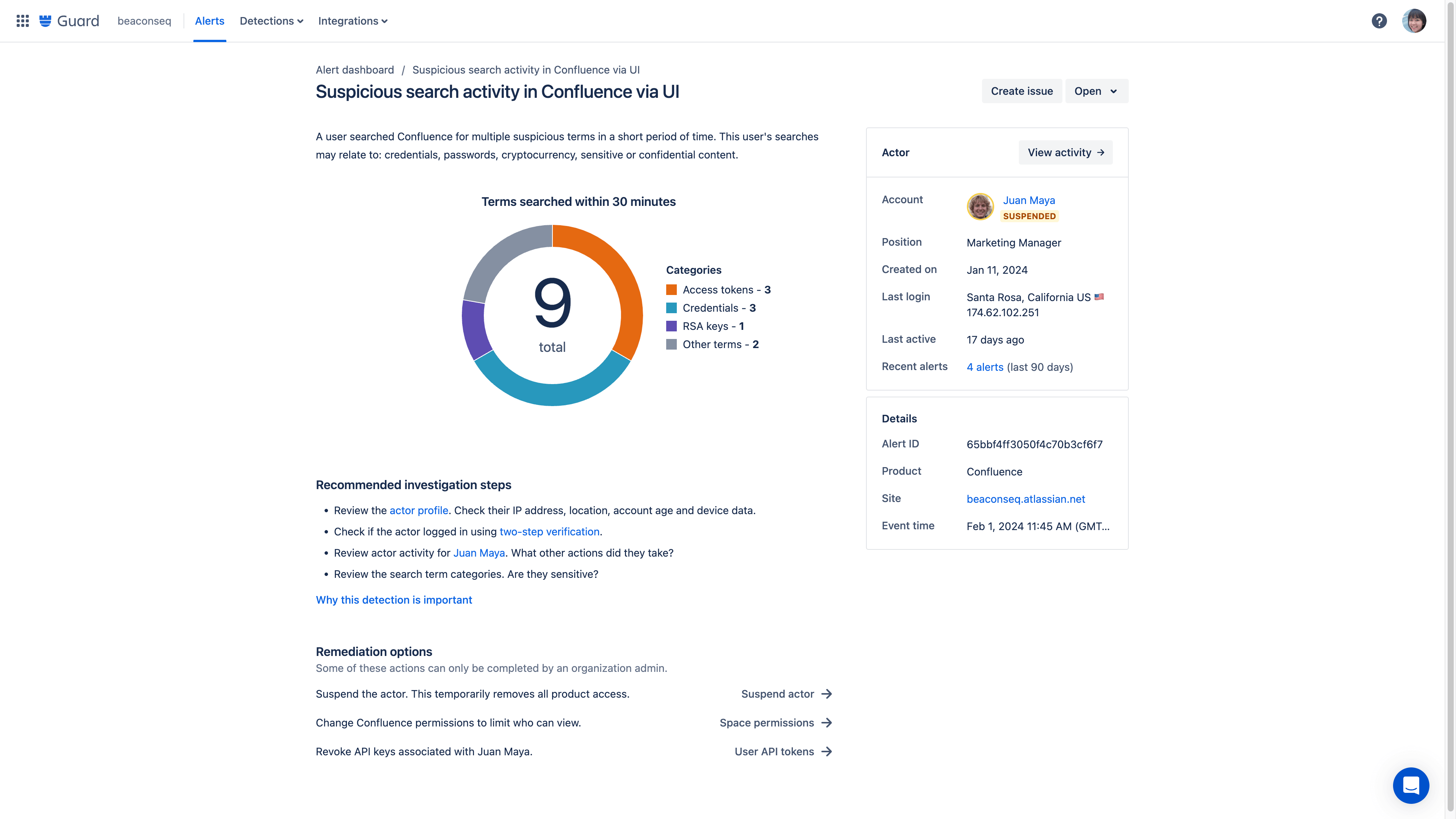
Anomalous activity detections provide intelligent oversight across your Atlassian cloud products by analyzing user activity and notifying you of potential risks. These queries search activity logs and alert you to any potentially concerning activity that requires review.
Content scanning
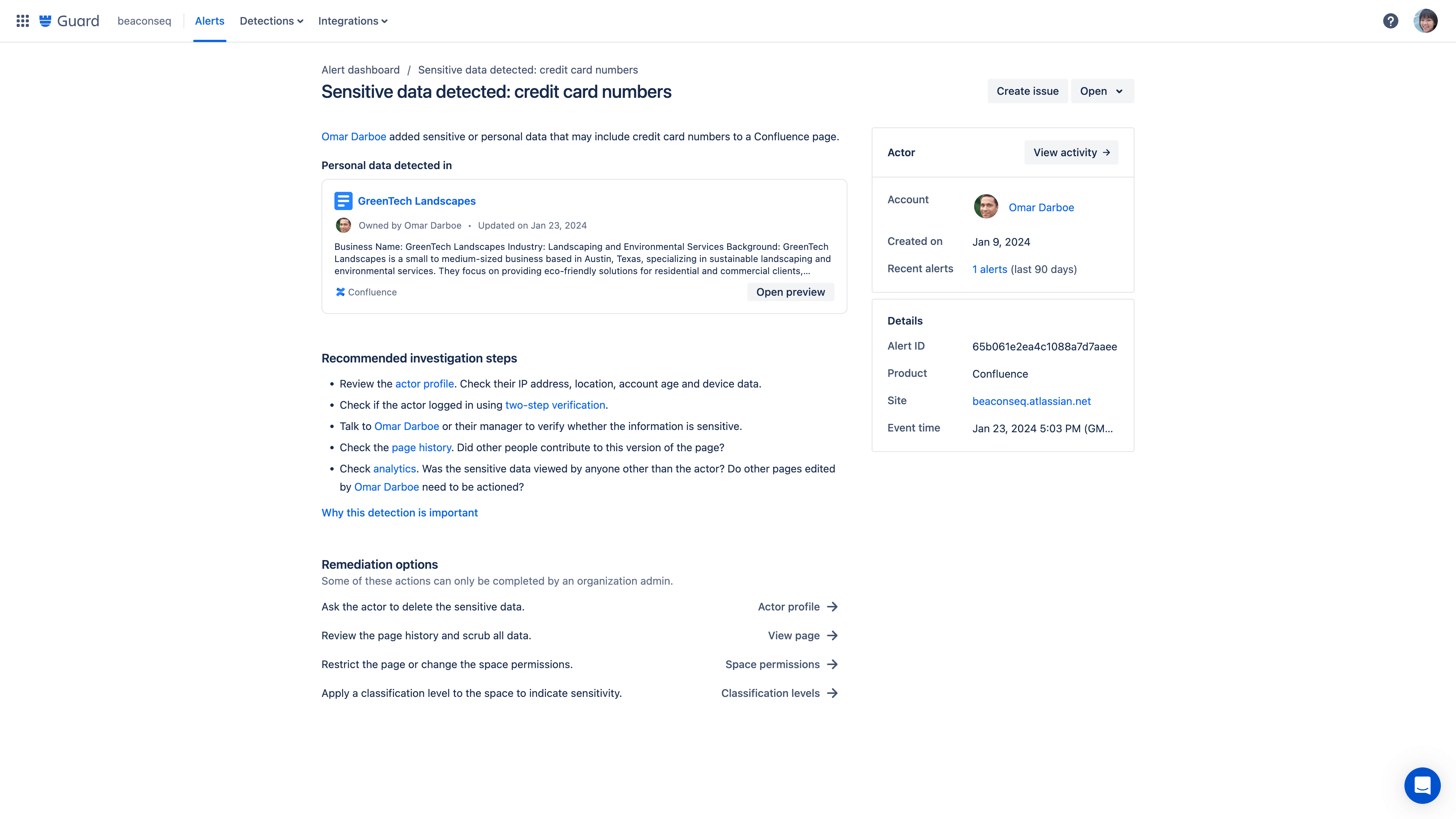
Content scanning detection rules monitor for critical data being added to Confluence pages. These detections generate alerts for any potentially concerning content that requires review.
SIEM integrations
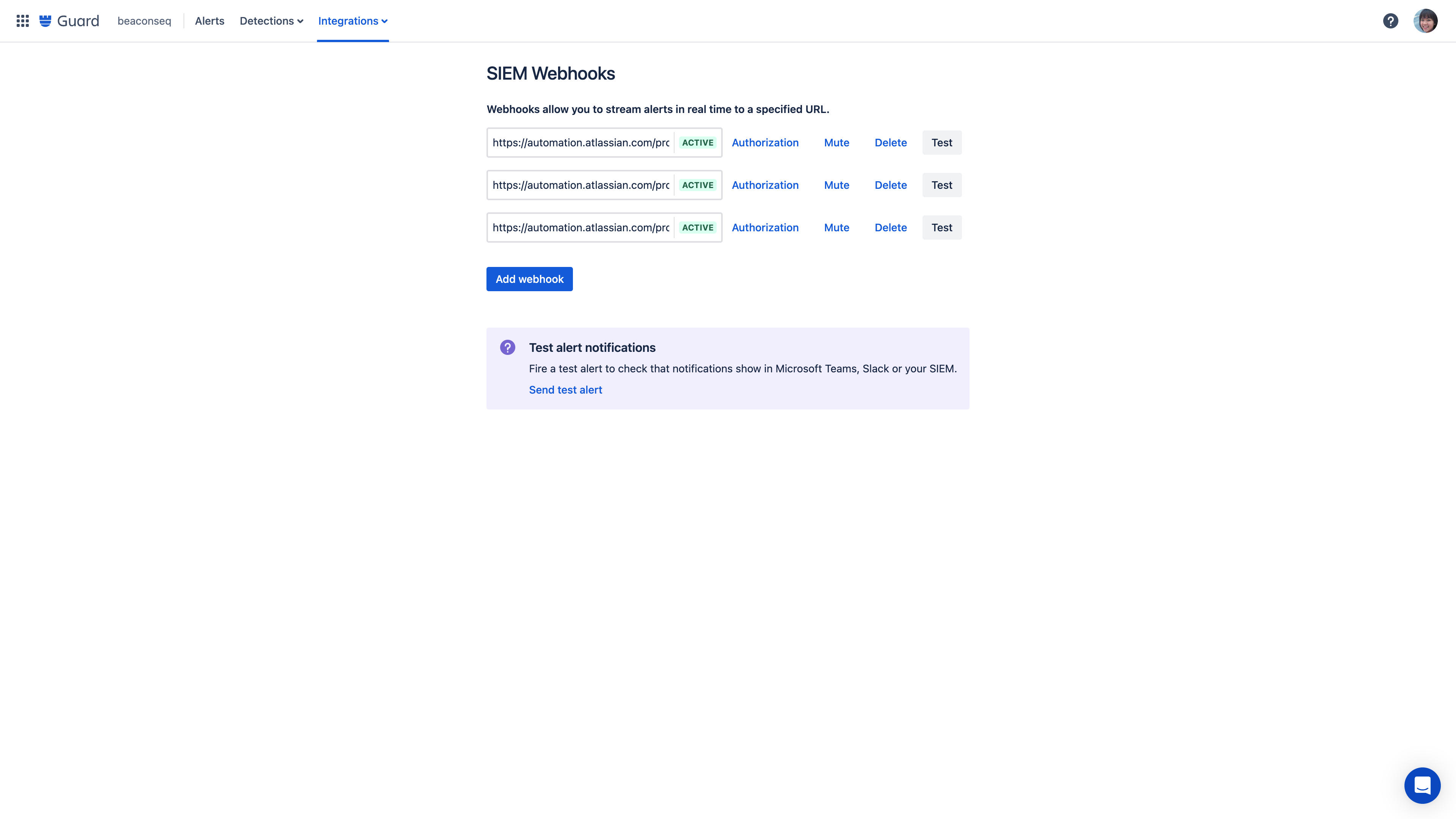
Using webhooks, send alerts about anomalous activity to any destination, including your organization-wide SIEM or an automation tool like Jira Automation, Zapier, or Workato.
Alert messaging integrations
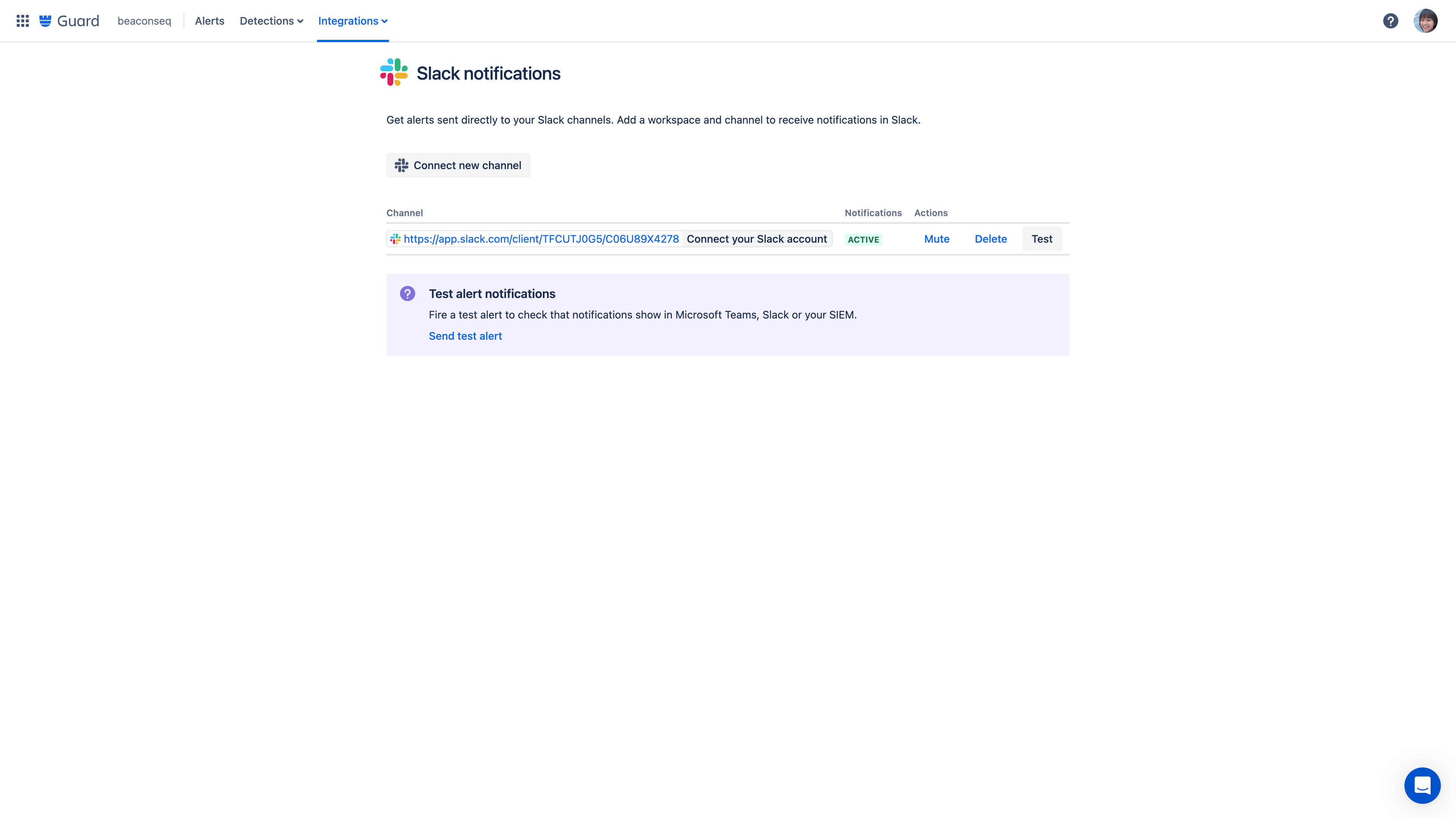
Integrate alert messages to your organization-wide tools like Slack, Microsoft Teams, and more.
Alert investigations
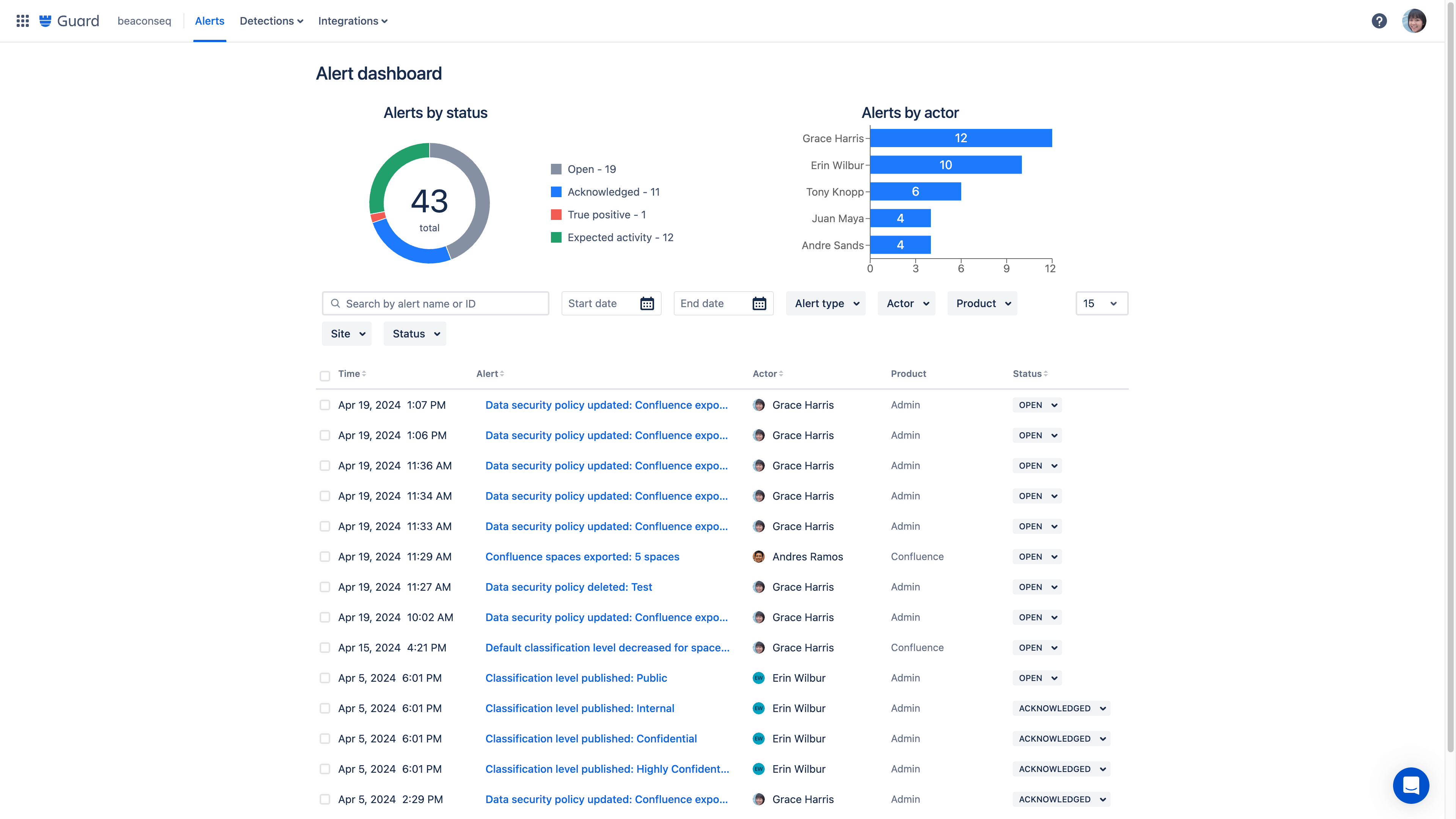
Alert investigations gives admins or security teams a consolidated view of potentially risky activity. Investigate the alert with details on what happened, which account was involved, other recent alerts tied to this account, and remediation options.
Actor profiles
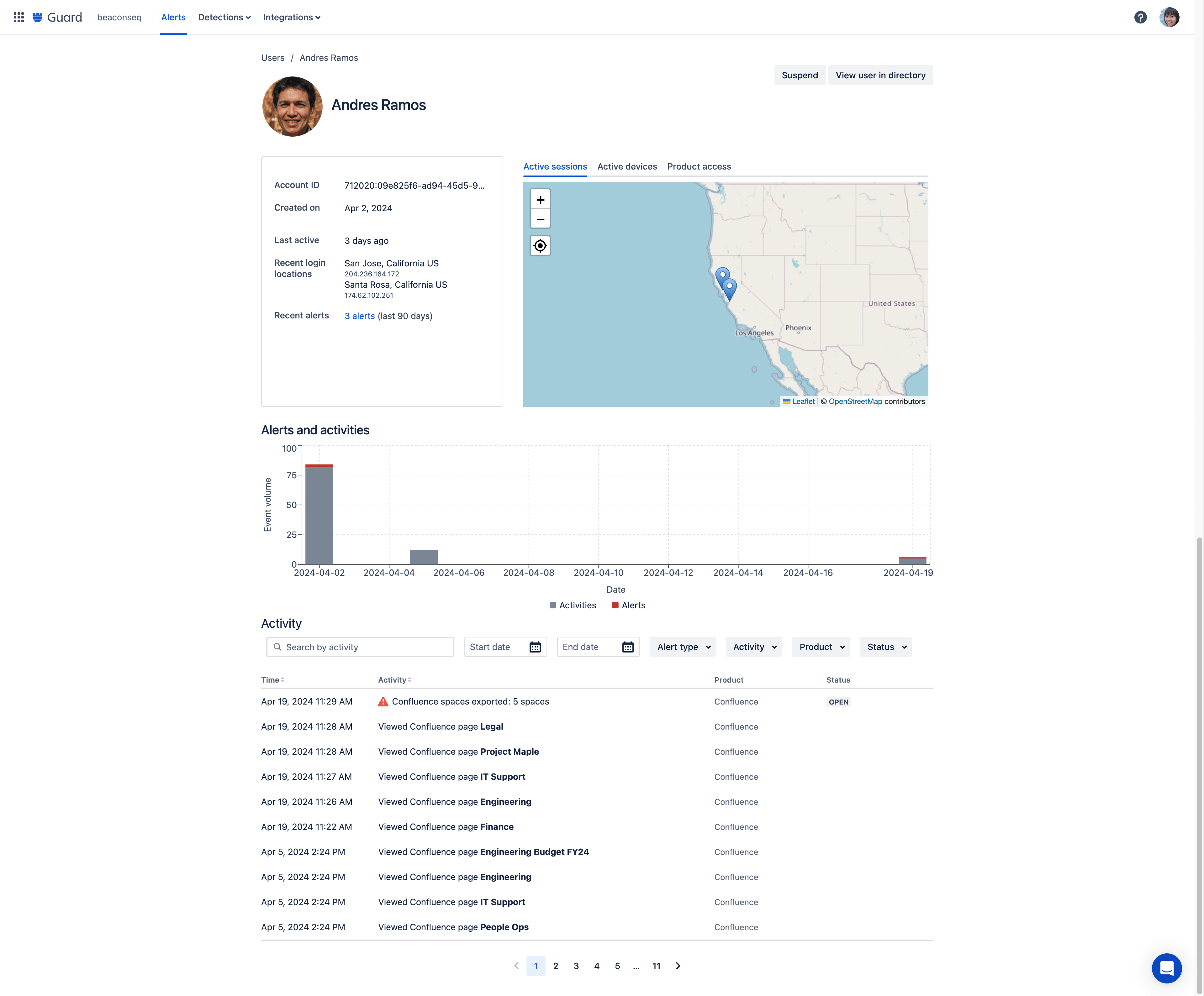
Access detailed user data by clicking into an actor profile directly from an alert to see a consolidated view of a user’s activity. On a single page, you can see a user’s role, location, recent activity, and a full list of their audit log alerts.
Remediation workflows

If suspicious behavior is detected, an organization admin can take action using the remediation recommendation to follow the suggested workflow and address a threat. Admins have the ability to immediately suspend a user's account directly from the alert dashboard.
Remediation recommendations
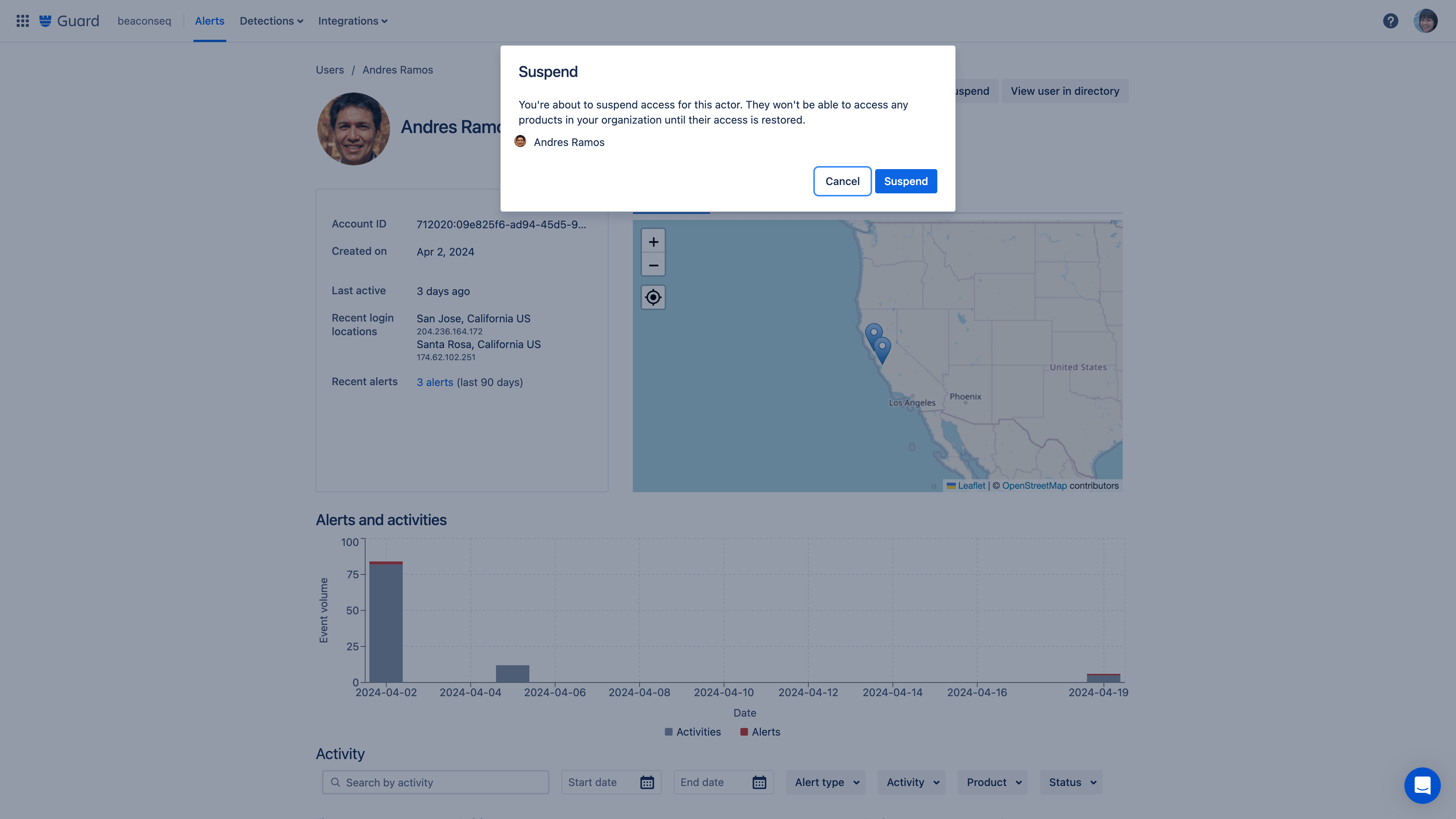
Respond to alerts faster with the ability to suspend a user’s account directly from the alert dashboard. Based on the actions logged in the dashboard, remediation options are recommended with actionable next steps.
Alert hand-off
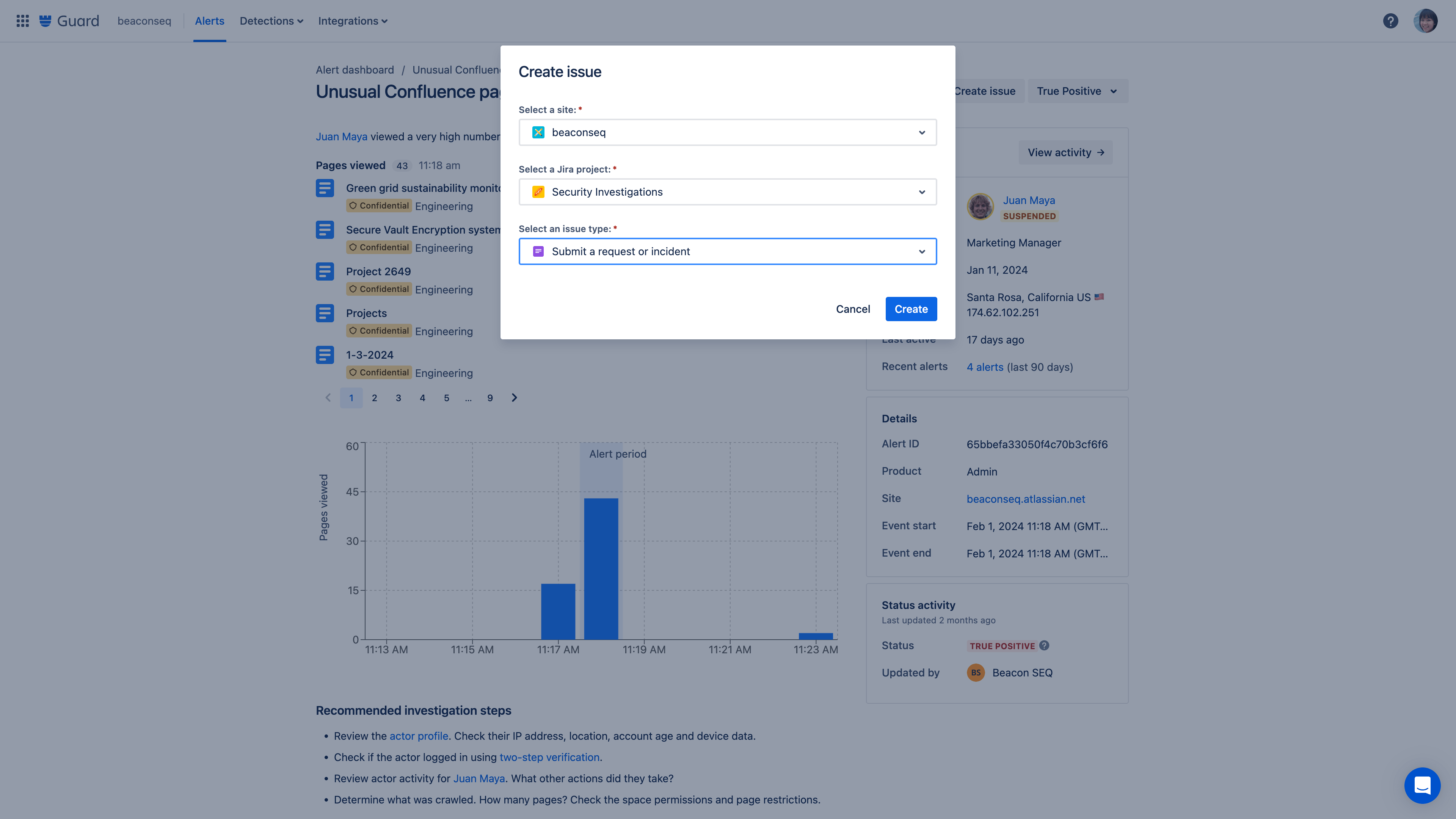
Connect an alert to Jira through the create issue button.
Questions about Atlassian Guard billing?
Visit our billing and licensing page for details.
Enforced two-step verification
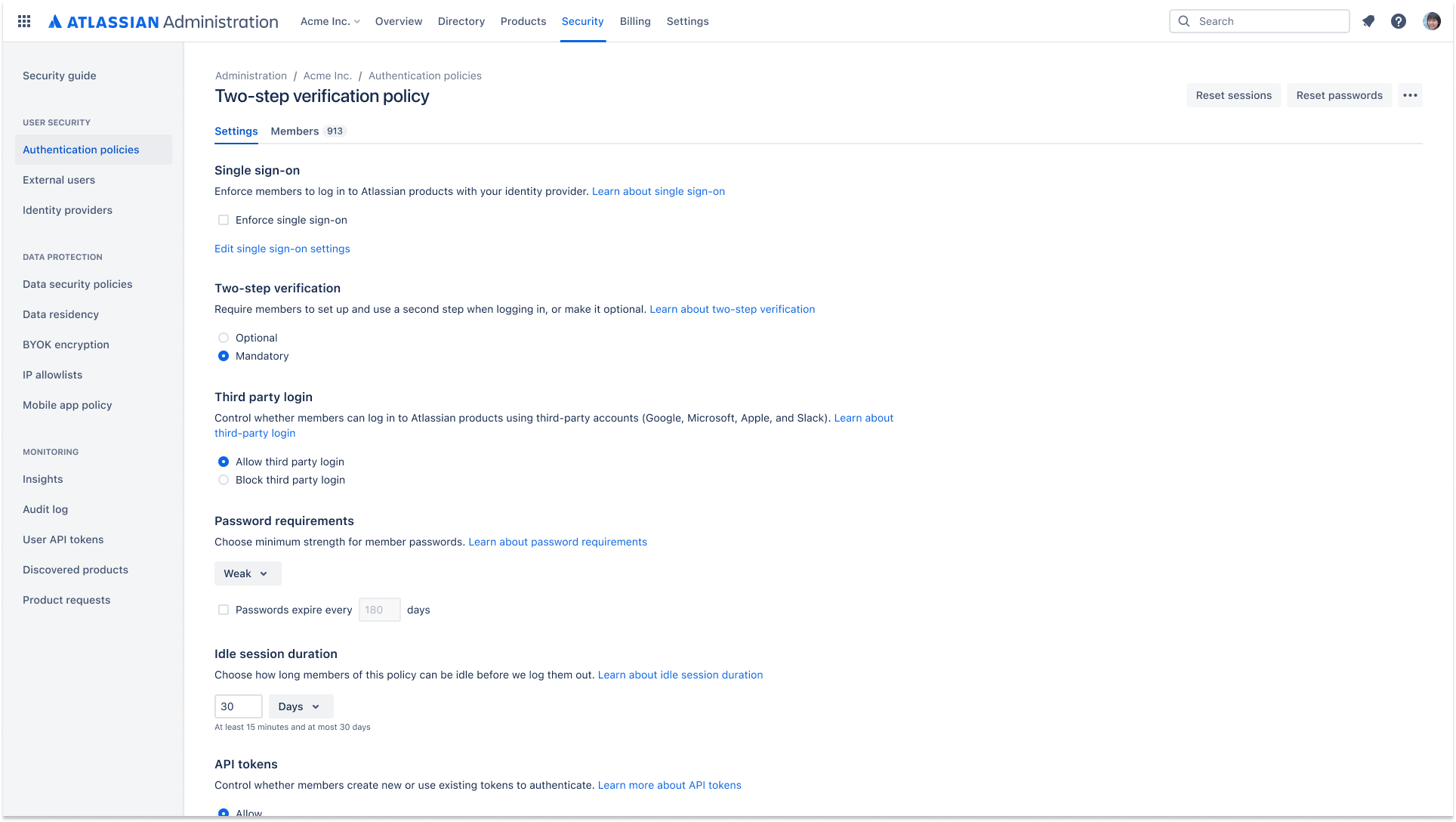
Enforced two-step verification can be applied as part of an authentication policy. This requires the users in an organization to turn on two-step verification in order to log in and access their Atlassian cloud products.